It’s Time to Upgrade Your Router
Chances are there are a couple of things about your current router that you would be much better off without.
But first, let’s discuss what is a router!
What Is a Router
A router is a hardware device that allows two networks to communicate with each other. The most common example is the router in your home or office, which allows your Local Area Network (LAN) to communicate with the Wide Area Network (WAN) provided by your Internet Service Provider. Without your router, it is likely all of the devices within your home or office would still be able to print and file share amongst each other, but browsing the internet, sending and receiving email, and even watching Netflix would not be possible.
Routers may provide connection to your LAN devices via ethernet (wired) or Wi-Fi (wireless).
Router Performance
A router may also be the weak point for both security and speed.
Lower-end or older routers are designed to work with just a few LAN devices. As the number of LAN devices increases, the router chipset becomes stressed attempting to handle the additional work. This results in slower network and internet speeds, router freezes, and odd behaviors like not allowing some devices to connect.
Higher-end and newer routers are designed to handle more LAN devices without overstressing the chipset.
How many devices do you currently have on your network? It’s quite easy to blow past the 5-10 devices your router is likely designed to handle. For example, in my two-person home we have:
- 6 computers
- 1 smartwatch
- 3 smartphones
- 2 printers
- 4 security cameras
- 1 security doorbell
- 1 hot water tank leak detector
- 6 smartTV’s
For a total of 24 devices on our Wi-Fi network.
Once you add in visiting friends or a business meeting, where each person may come with 2-3 devices (smartwatch, computer or tablet, and smartphone), and those numbers can easily hit 50+ devices.
If you have been unhappy with your LAN or WAN performance, the solution may be as simple as a new router that can easily handle all your devices.
Router Security
As is typical, security is my bigger concern.
Older routers are designed with WPA or WPA2 (Wi-Fi Protected Access). This protocol is intended to help keep all Wi-Fi data secure. But as you know, security and privacy are a cat-and-mouse game. WPA is now easily cracked and should never be used. WPA2 can be cracked, although it takes some determination.
In January 2018, WPA3 was released. To date, it is the most secure option available and is generally considered uncrackable (although testing has found some flaws). If your router has WPA3, network security should no longer be your biggest concern.
Modern Router Performance and Security
With routers that have first been available for sale since 2018, WPA3 security is included. So any modern router has the best security built-in.
In addition to WPA3 security, modern routers that have first been available for sale since March 2021 will have a huge performance boost in the form of 802.11ax (Wi-Fi 6). Wi-Fi 6 not only has faster performance overall than the previous 802.11ac but can handle far more devices and traffic without stress. In fact, with a Wi-Fi 6 router, your Wi-Fi 6 devices can communicate faster over Wi-Fi than over ethernet (based on proximity).
There is a recent update to Wi-Fi 6 called Wi-Fi 6E. Wi-Fi 6E includes a frequency range that hasn’t been used before (6GHz). If you have new devices that can operate on that frequency, they can operate even faster as their channel won’t be congested and competing with other devices.
At the moment, there are only a few devices that are capable of using Wi-Fi 6E, but most new devices from now on will include it.
Finding a Wi-Fi 6 or 6E Router
Browsing over to Amazon, then searching for “router Wi-Fi 6” will display most of the current crop of routers. There are more than a dozen quality manufacturers, but my preference for most home and small-medium-sized businesses is ASUS. ASUS is consistently among the top-rated for:
- Quality parts
- Quality construction
- Overall performance
- Features
- Security
High-End
At the top of the heap is the ASUS GT-AXE11000. It simply doesn’t get any more secure, faster, or more expensive than this. This unit is tri-band, including 2.4 GHz, 5 GHz, and 6 GHz, making it future-proof (well, when it comes to technology, that means it should serve you well for the next 5 years). As with all of the better ASUS products, it includes Trend Micro security, automatically checking for malware, malicious websites, and other things that cause me nightmares.
Midrange
The ASUS GT-AX11000 is the GT-AXE11000’s little brother. They look similar and have similar specs. Where the AX11000 is different is that its tri-band is 2.4 GHz, and two 5 GHz bands. Having two 5 GHz bands will make this unit a better solution today (as there are so few 6 GHz devices to connect with it), but it isn’t future-proof. As you replace your current devices (computers, tablets, phones, etc.) the new devices will be 6GHz.
Low-End
If your needs are modest and have only around 5-10 devices to connect to your router, you will be quite happy with the ASUS AX6100 router. As with my other two choices, this comes with Trend Micro security, and is tri-band, with 2.4 GHz, and 2 5 GHz bands.
Configuring Your Router
If there is a downside to using a better router, it is that they are not plug-and-play. They do require a small bit of configuration. But it is nothing you can’t do with a little help from your friends 😉
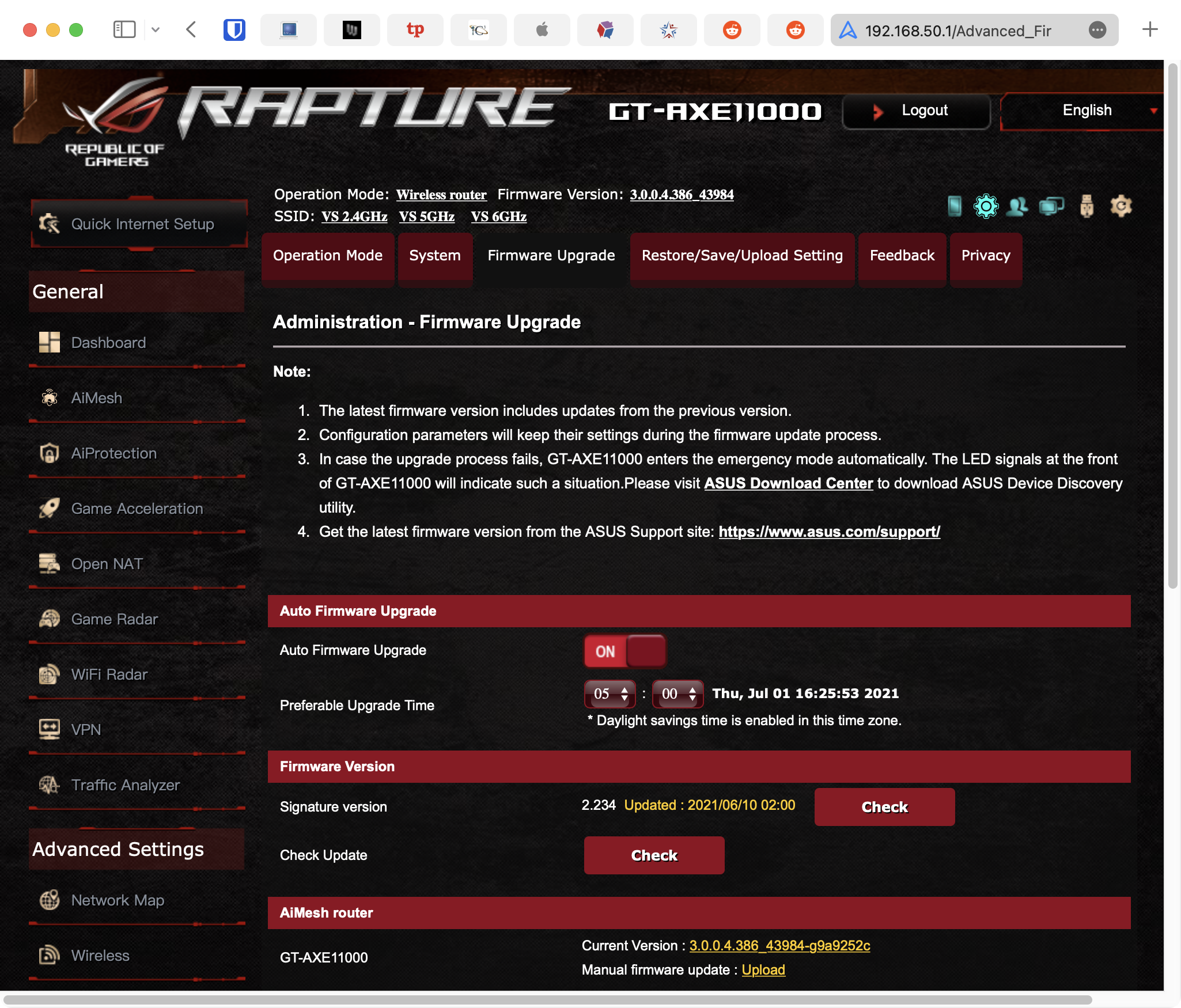
Although every router configuration portal is different, I’ll show how the GT-AXE11000 looks.
- Connect the router to your network.
- Open a browser, then enter the router IP address. The router authentication screen opens.
- Enter the router default administrator name and password, then tap OK.
- In the configuration portal, from the sidebar, select Wireless. The main area of the page allows the configuration of the three bands (in this case, 2.4 GHz, 5 GHz, and 6 GHz).
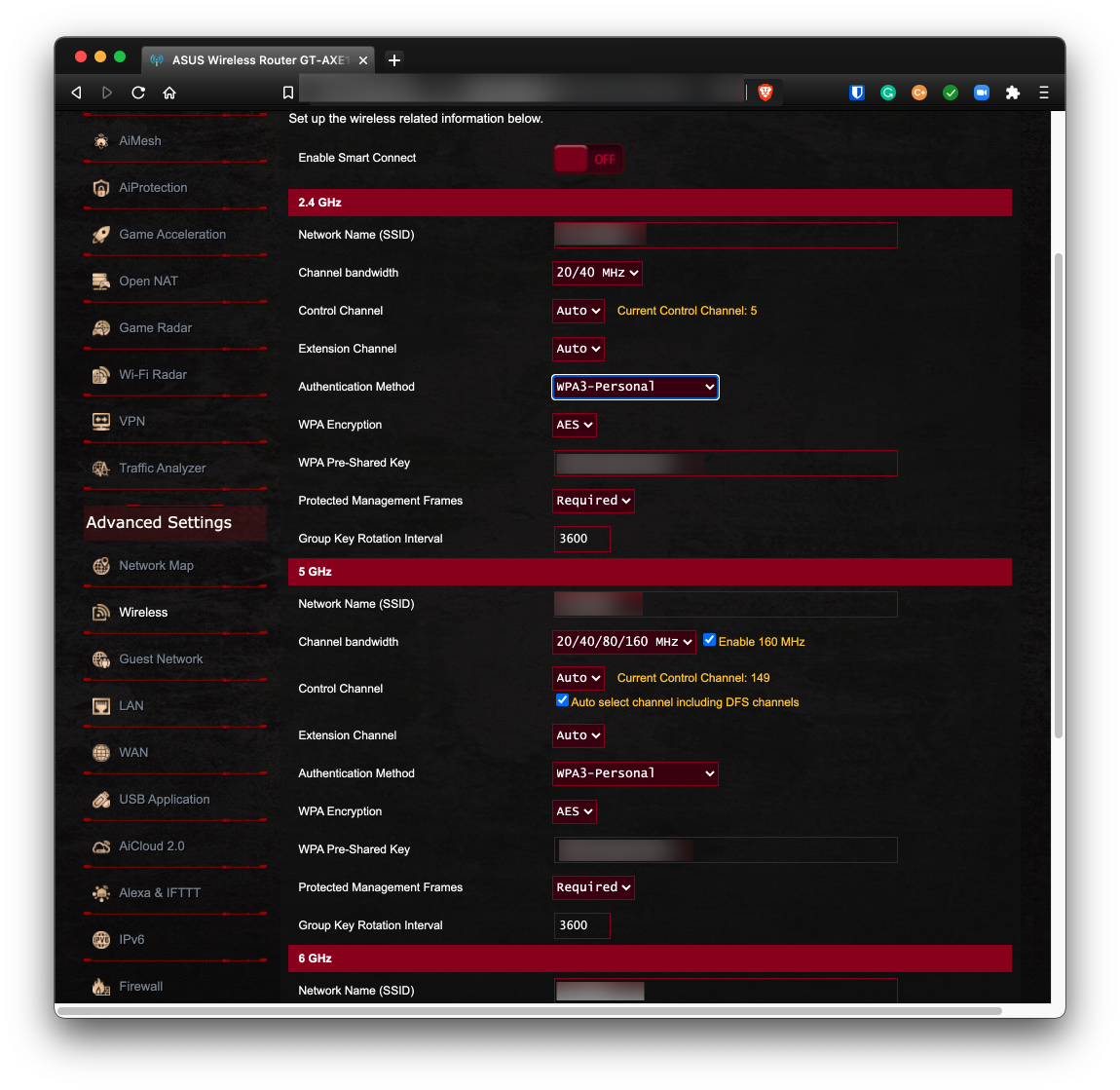
- For each of the bands, in the Authentication Method areas, select WPA3 Personal.
- Tap the Save button, then exit from the configuration portal.
- On each of your devices that will connect via Wi-Fi to the router, you will need to reconnect by selecting the Wi-Fi network, enter the password, then tap OK or Connect.
- That’s it! See, not so tough.