Q: How Do You Verify a Gmail Account
Q: How Do You Verify a Gmail Account?
A: If you mean how does one verify that a gmail account belongs to who it claims… no method is available that is reasonably accurate.
A: If you mean how does one verify that a gmail account belongs to who it claims… no method is available that is reasonably accurate.
A: This is very much like asking is it possible for a virus to wipe out all of humanity on the planet.
Even Ebola doesn’t have a 100% kill rate.
In the case of a computer virus, the virus would need to be compatible to run on 100+ different operating systems, able to read and write to many different storage device formats, and act fast enough so that it is able to attack worldwide so quickly no defense mechanism could be put in place (probably faster than 24 hours). It would also need to impact backups of backups of backups. Of which, most are read only – so cannot be erased, encrypted, or changed.
I’m sure there are at least a dozen other major hurdles it would have to overcome.
Overcoming one or two of these issues is easily doable. Overcoming all of them? It is not within the reach of technology as we know it today.


As a people, many of us are outraged, perhaps horrified, at recent actions and the direction taken by our elected (and a few who are not elected) officials. There are others who are outraged that we are outraged.
An overwhelming amount of emoting and shouting from all sides.
Perhaps it is a time for a bit less talk, a bit more thought.
Thought about where our energy is best spent. Ranting on social media is not as effective as a well thought out communication with our political representatives. Am I under some delusion that any of my representatives gives a damn for my thoughts and opinions? Not at all. I am not on their radar, because I did not provide a non-trivial financial contribution to their election, or slip $$$ into their hands. But every letter, email, and phone call is logged as to where this voter stands on issues. If the log weighs heavily to one direction – heavy enough to place reelection in jeopardy – now collectively we are on the radar.
But first, each of us must know who our representatives are. Lucky for us, that information is just a click or two away.
Common Cause makes the task a no-brainer. They have a web page dedicated to providing all of your representatives, simply by entering your address:
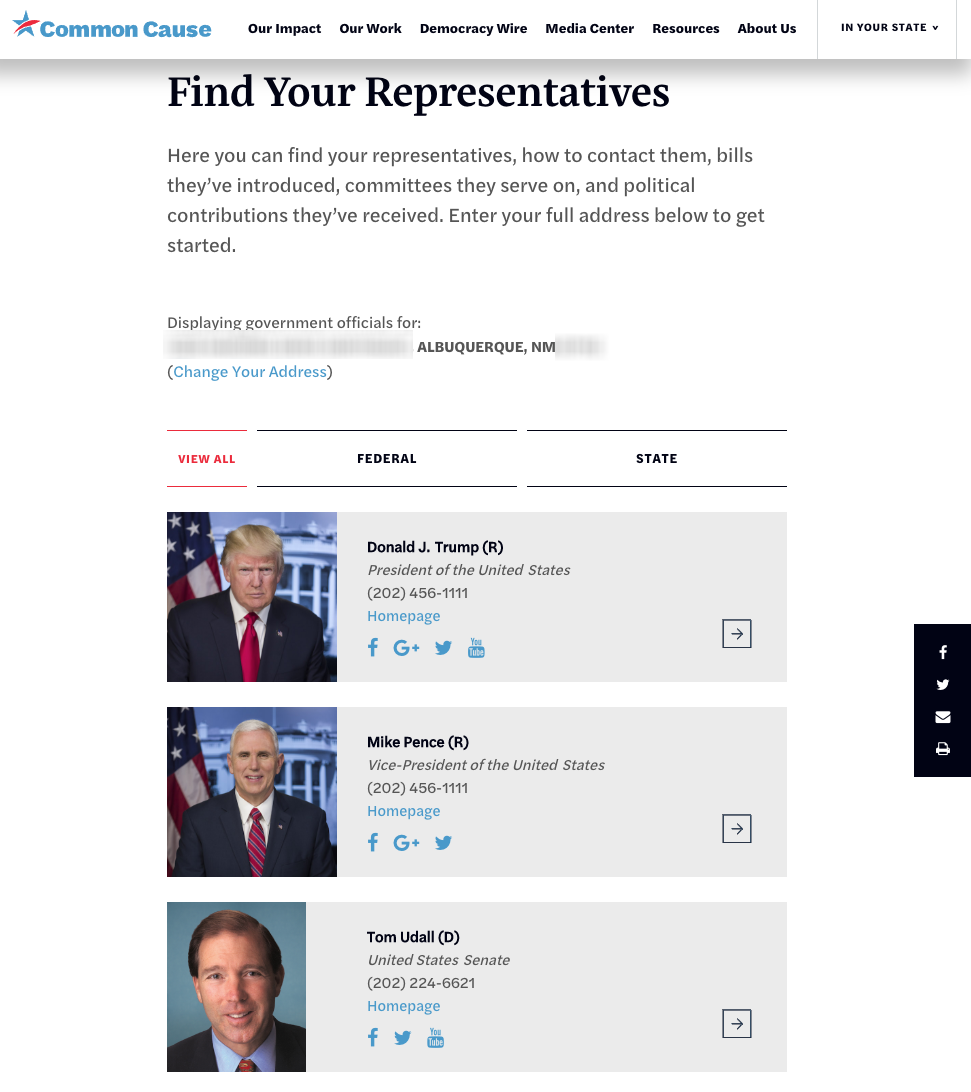
November is just around the corner. It is time to be the change you wish to see in the world.

My older readers may remember the letter written by Martin Niemoller:
When the Nazis came for the communists,
I remained silent;
I was not a communist.
When they locked up the social democrats,
I remained silent;
I was not a social democrat.
When they came for the trade unionists,
I did not speak out;
I was not a trade unionist.
When they came for the Jews,
I remained silent;
I wasn’t a Jew.
When they came for me,
there was no one left to speak out.
As reported by PBS on June 28, 2018, even as the White House faces court orders to reunite families separated at the border, immigrant children as young as 3 are being ordered into court alone for their own deportation proceedings.
We as a people cannot be silent. If you can stand your heart being crushed by what our country has become, I urge you to read the article.

From the first posting to all of my website blogs and social media, I have focused solely on IT, and primarily on IT security and privacy. I have blocked all friend/member comments and postings that have not had a similar focus.
This is because, from my perspective, security and privacy are foundational to everything else we hold dear in life. Without security and privacy, all else is lost.
As of today, I have upgraded my focus. I have added Humanity and Compassion to the foundation.
The triggering mechanism for my upgrade is a sociopathology that has taken root in our political system. I am deeply and profoundly concerned that the core values on which this once-great country is founded (although not often followed) have been thoroughly corrupted. Humanity and compassion for the 98% have disappeared.
As a people, we are being consciously, willfully, and meticulously divided (divide and conquer) on a daily, if not hourly basis by those elected to serve us, but who now only serve the 2%.
Those who openly oppose or question this process are oppressed, sometimes to the point of death.
Which makes security and privacy all the more important. But if we lose our humanity and compassion, what is it we are protecting in this culture?
So, yes, going forward there will be sociological and political entries here. For some of my followers, these may induce a knee-jerk reaction of upset. I don’t ask that you agree with me. I do ask only that you take time to be thoughtful, not only with what is presented and your reaction to it, but also how each of us can be the change we wish to see in the world.
Warmly,
Marc L. Mintz

When the Department of Homeland Security makes a public cybersecurity announcement, we should all wake up, listen, and pay heed. This is one of those times.
Update: Thursday, May 24, 2018.
As reported in The Beast, the FBI claims to have found the key server responsible for penetration and compromise of over 500,000 routers. The server is linked to the Russian criminal hacker group Fancy Bear. This is the same group that breached the Democratic National Committee and the Hillary Clinton campaign during the 2016 election.
With the seizure of the server by the FBI, the compromised routers are no longer being “controlled” by the server. As such, performing a power cycle (power off, wait a minute, and then power on) will clear the malicious code from memory (stage 2 and stage 3 of the malware). For those devices with stage 1 present (infection of the firmware), the power cycle will not clear the code. It is recommended to upgrade any machines that are on the compromised models’ list to remove the malware. However, as the server is no longer issuing instructions or harvesting data, the risk of data harvest is dramatically reduced. The risk of instability and unpredictable behavior is still present until the new firmware is installed, removing the malware.
Now, back to the original story…
First, I apologize. I wish with all my heart that my job was to deliver candy (or beer), flowers, and baby alpaca to each of my clients on a regular basis. But I tried running an alpaca ranch and lost my shirt. So now I just get to deliver harsh realities as part of my job to prevent even harsher realities from steamrolling my clients.
As reported in the Department of Homeland Security US-CERT report this morning (May, 23, 2018), a critical vulnerability has been found in network devices manufactured by Linksys, MikroTik, Netgear, QNAP, and TP-Link (and very possibly many others).
The vulnerability has been named VPNFilter. It has three primary features:
Although the report is preliminary, it appears VPNFilter has been active for at least two years, with at least 500,000 devices in at least 54 countries impacted.
What is particularly malicious about this malware is that, unlike most of its kind, it will survive a power cycle or device reboot.
Talos, the organization that first discovered VPNFilter and continues to research it, has the following recommendations for everyone who has a Linksys, MikroTik, Netgear, QNAP, or TP-Link (and really, any network) device:
More technical details may be found at here at Talos.
Sincerely,
Marc L. Mintz, MBA-IT, ACTC
888.479.0690
marc@mintzit.com

Thanks in part to the recent Facebook role in Russian-financed election meddling, and to the General Data Protection Regulation (GDPR) going into full effect in a week, websites and organizations are having their arms twisted to provide at least some level of transparency into how they collect and use your data.
Most of us use the internet with free abandon–never giving thought as to how this site or the next provide such wonderful conveniences and benefits without asking anything in return. But this is a Faustian bargain. In many cases, everything you do before, during, and after your site visit is logged. Many of these sites truly do know more about you than your mother.
To give just one example (more to come in the following weeks), let us look at the Privacy Agreement for Yahoo and AOL, now part of Verizon and the Oath. The full text of the agreement may be found at <https://policies.oath.com/us/en/oath/privacy/index.html>.
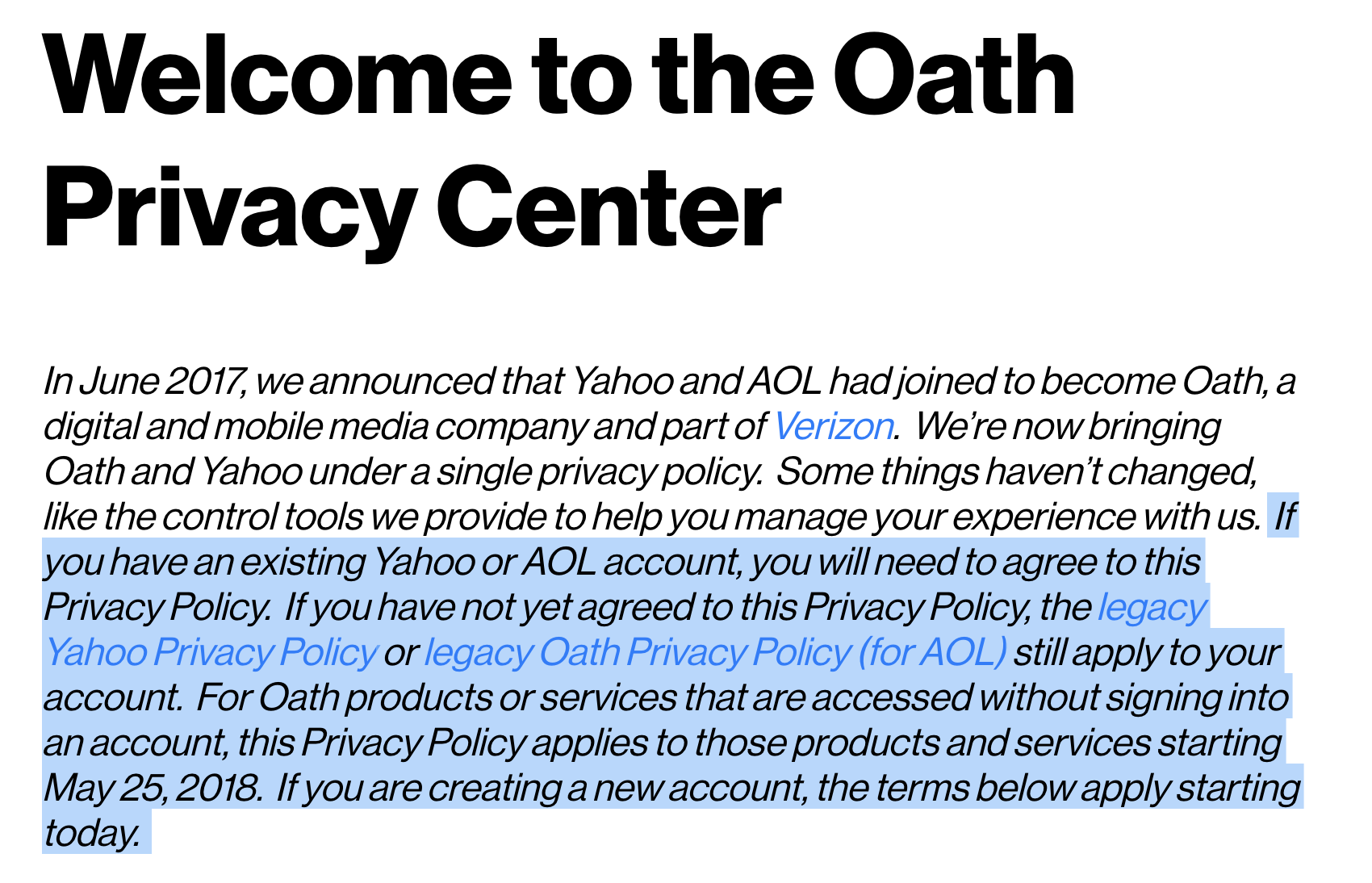
Understand that:
A) If you have an existing Yahoo or AOL account, you need to agree to this policy.
B) If you haven’t agreed to this policy, it will go into effect May 25, 2018 regardless of your agreement status.
C) In otherwords, we don’t give a damn about what you think, say, or do. This agreement applies to you.
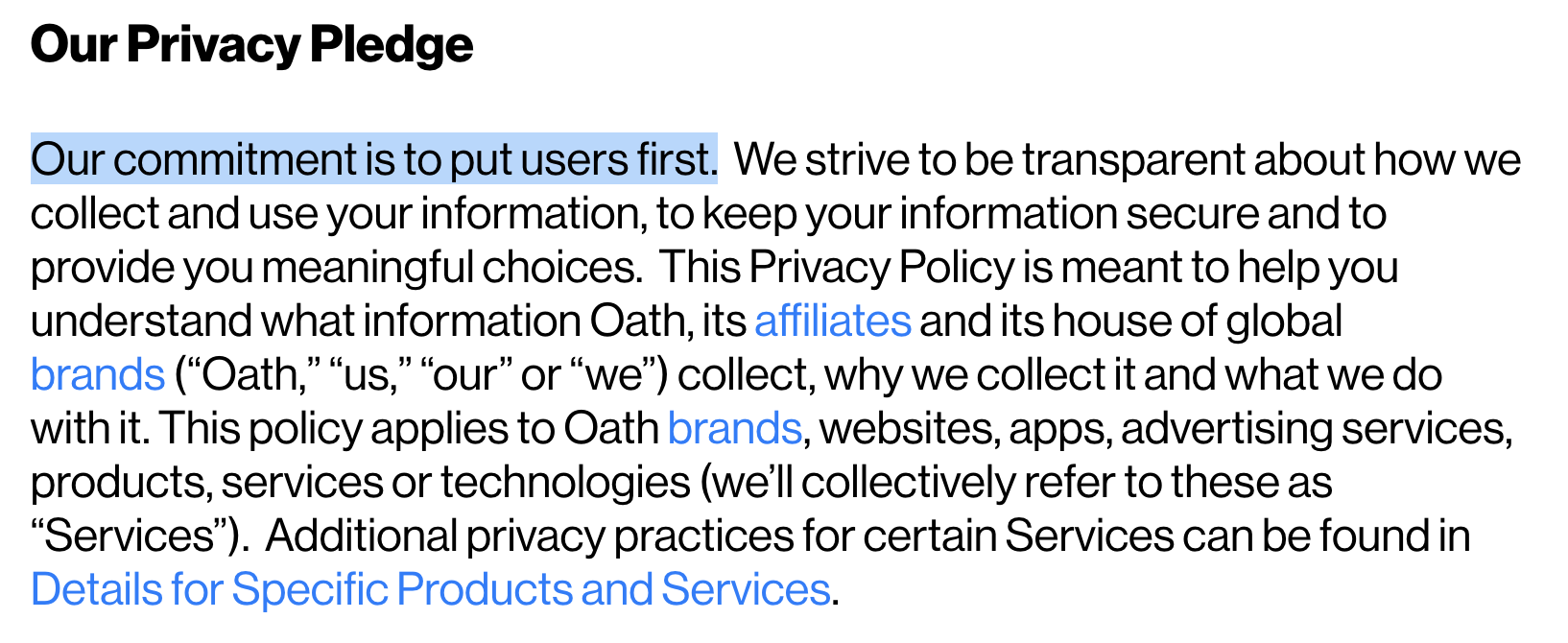
I feel all warm and fuzzy inside knowing that they “put users first”. Well, not really. If they put users first, you and I would have had opt-in options long ago, instead of being automatically opted in. Somewhat contradicting the draconian first paragraph.
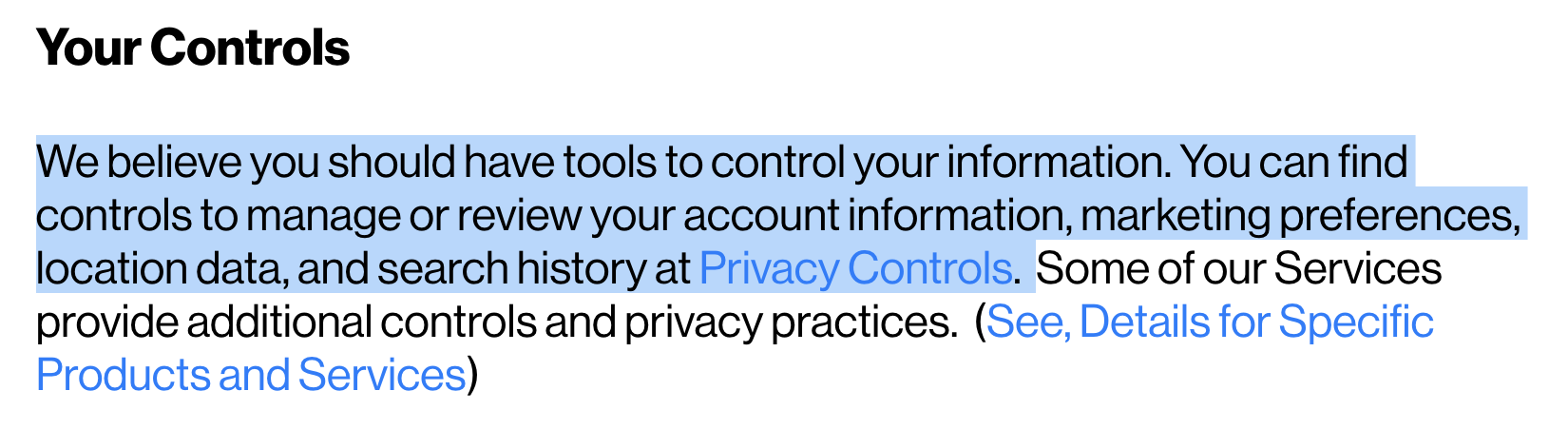
If they believed you should have tools to control your information, why did it take so freakin’ long for them to let us know they even existed? Why no opt-in options, just automatic opt-in.
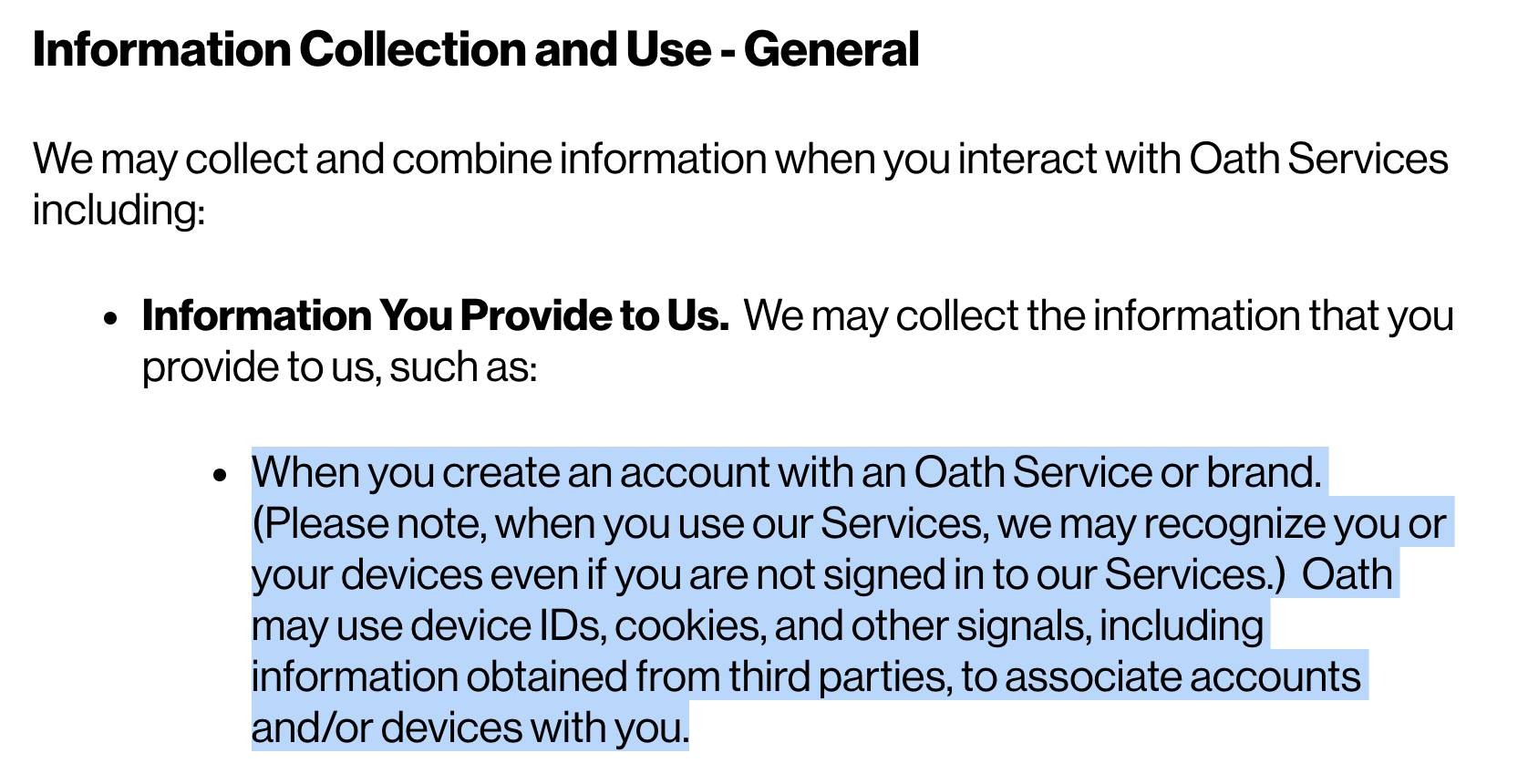
When you create an account with Yahoo, AOL, Verizon, or any one of the many other Oath brands, you are giving them permission to track your online activities, giving access to your device, ID, cookies, even data available from non-Oath services.
The next two paragraphs get even better:

You read this correctly, you have willingly or unwillingly (they really don’t care. Remember the first paragraph?) agreed to allow them to read, analyze, log, and sell information regarding your PRIVATE photos, voice, video, emails, texts, and attachments.

They are just telling us again (remember, this is about transparency) that they will track you by your device, harvest whatever they can not only from the device, but also third-parties. All to provide you with “personalized experiences and advertising across the devices you use.”
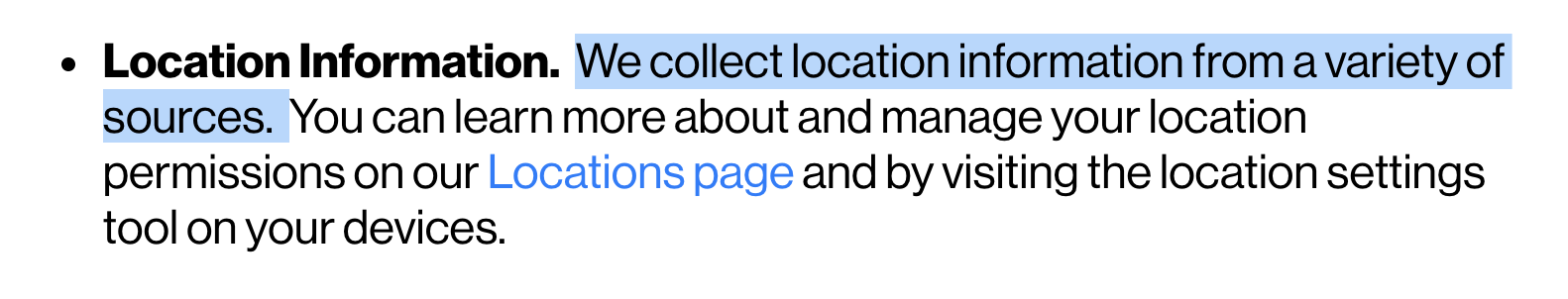
Not only are all of your online activities monitored, recorded, analyzed, and sold, but you have given permission to track your location. Remember, your cell phone is nothing if not a location beacon.
The Privacy Agreement goes on for another few pages, pretty much just repeating itself over and over. I suspect the real purpose is to put the reader into a trance-like state so that ramifications of the agreement simply cannot sink in.
It may bear remembering that one of the Oath companies that you have just given away all your privacy rights is the same company that had not 1, but 2 of the largest security breaches in history. Yahoo. Yeah. That’s who I want to continue harvesting my data.
Understand that the only thing the enterprise is concerned about is money. Not you, not me, not doing good, not serving society. Money.
The Oath brands can be found at <https://www.oath.com/our-brands/>, and include: AOL, Autoblog, BrightRoll, Build, Built By Girls, Engadget, Flurry, Huffpost, Kanvas, Makers, Rivals, Ryot, TechCrunch, Tumblr., Verizon, Yahoo,
Have a heart-to-heart with yourself as to whether or not you want to give money to an organization that treats you like this. And if you decide it is not such a good trade, stop doing business with those who do not have your best interest in mind. There is a competitor available. Always.

Practical Paranoia iOS 11 Security Essentials version 2 has just been published. All of the changes since version 1.0.1 are included in the attached pdf. Changes are from chapters on Passwords, Lost or Stolen Device, Local Network, Web, Email, Internet Activity, and Social Media.
Over the past 30 days, more than 20,000,000–that’s right, 20 MILLION–email accounts have been hacked.
Only around 80% of email providers support TLS. TLS is what allows your email be sent encrypted, received encrypted. Even if the email provider supports TLS, there is no way to know if the recipient is using an email application that supports TLS.
Simply dealing with email encryption is beyond most users. Heck, it is beyond most IT consultants.
Not only is email encryption beyond the skillset of most consultants, it is beyond those of Phil Zimmermann, the cryptographer who invented PGP! PGP is the granddaddy of all email encryption. In a recent interview, he said he himself has stopped using PGP because of difficulties with it.
Email is a wonderful, but legacy, technology. As such, it brings all of the legacy shortcomings along for the ride. Email was never designed for security, so any security option has to be bolted on. And this introduces bugs, conflicts, costs, and migraines.
So I have to ask you, Why are you still using email?
My guess is inertia. It’s what you have used to communicate for so long, it has become a boat anchor that feels like an old friend.
The younger the user, the less they use email. In fact, it is unusual to find teens using email at all. Instead, they use instant messaging.
The great thing about instant messaging (when it is done right) is it can be created from scratch with security in mind. This eliminates all of the problems associated with encrypting email.
At the moment there are two leaders in the end-to-end military-grade encrypted instant messaging area: Signal (https://signal.org), and Wire (https://wire.com). One is as secure as the other.
My personal preference is Wire, because it is available on Android, iOS, macOS, Windows and anything that can open a web browser. Wire allows fully secure instant messaging, voice calling, and video calling. You can encrypt attachments, and even schedule when a message self-destructs.
Wire is free for personal use, for-fee for business team use.
Signal is free for everyone.
The only reason I can see for not using Signal or Wire is an organization that has a compliance requirement to maintain a record of all communications. This is typically only the healthcare (HIPAA) and financial (SEC) industries. For everyone else, Give up your phone, turn off your email, get a Wire account. Save some money, secure your communications, and sleep better at night.
Warmly,
Marc L. Mintz, MBA-IT, ACTC, CWT
President & CIO
Mintz InfoTech, Inc.
505.814.1413 x 1
Wire: @marclmintz
Signal: 505.453.0479

As reported by the Electronic Frontier Foundation (EFF) this morning <https://www.eff.org/deeplinks/2018/05/attention-pgp-users-new-vulnerabilities-require-you-take-action-now>, a group of security researchers found a set of vulnerabilities impacting users of PGP, GPG, and S/MIME. These are the considered the cornerstones of encryption security for email. The vulnerabilities pose an immediate risk of exposure not only of any email sent going forward, but also to all those encrypted emails in storage.
The EFF is recommending that all users of PGP, GPG, and S/MIME “immediately disable and/or uninstall tools that automatically decrypt PGP-email. Until the flaws described in the paper are more widely understood and fixed, users should arrange for the use of alternative end-to-end secure channels…”. MintzIT is recommending the use of Wire <https://www.wire.com> or Signal <https://www.signal.org> for secure end-to-end messaging.

Practical Paranoia macOS 10.13 Security Essentials has just been updated with many additions. So many, we have combined them into a single update for chapters 13, 14, 15, and 16.
Revisions include:
Download the updated chapters here: Practical Paranoia macOS 10.13 v2.1b 20180513 Chapters 13, 14, 15, 16

Your communications through email have become one of the most highly prized targets of criminal hackers. Your email contains literal keys to your kingdom:
Changes in the technical management of email now give us the tools to help fight back, and protect your email security and privacy. It is now time to make use of these tools because the bad guys pick on the vulnerable.
Gather the following information:
SPF (Sender Policy Framework) is an email-validation system. Its job is to detect spoofed email. When a criminal hacker sends email to you with fake “from” information (say perhaps, a Nigerian Prince? Or a vendor submitting an invoice for payment? How about an attorney threatening to sue unless they receive payment?), your email server is able to validate or invalidate the sender.
If the sender of an email is validated, the email comes on through as it always has. If the sender is invalidated, the spoofed/fake/junk email simply never makes it to your inbox.
Not only does this help prevent fake email from making it into your inbox, it also helps to prevent anyone from sending fake email using your email address or an email address with your domain.
Implementing SPF for your domain email is usually quick and easy, but it does require modification to your DNS records, and the record values are different for each email host. For this example, we will use Google.
DKIM (Domain Keys Identified Mail) is another email authentication protocol designed to detect email spoofing. DKIM verifies that email that claims to have come from a domain is authorized by the owner of that domain. It is able to prevent the criminal from forging your email address, as is often done in phishing and email spam.
As with SPF, implementing DKIM requires access to your DNS records. The process is a bit different with each email host. In this example, we will use Google.
Now that the DKIM is in place, we need to automate the process of including it with each email sent from your domain. In this example, we will use Google.
DMARC (Domain-based Message, Authentication, Reporting & Conformance) is the configurable policy for how to handle email that fails DKIM validation. The options are to take no action, quarantine the email, or reject the email.
For DMARC and DKIM to work, all of your email must be sent through your own domain, not through a different domain, or forwarded through a different domain.
Although 2-Factor Authentication (sometimes called 2-Step Verification or Multi-Factor Authentication) is a completely separate security protocol, this is a great time to finally get to this honey-do item. In todays IT environment, having 2-Factor Authentication is the only thing stopping the criminal from taking control of your email.
Not every email provider makes 2-Factor Authentication available. If yours does not, RUN to a different provider–one that takes your security and privacy seriously. If your email provider does make 2-Factor Authentication available, find their help page for how to configure. Each provider will have a different authentication process.
MintzIT holds higher IT certification, more certifications, more years of experience, and more customer commendations than any other IT consultant in New Mexico. We will make this a quick and painless process for you and your organization. Please feel free to call for a quote.
Warmly,
Marc L. Mintz
President & CIO
Mintz InfoTech, Inc.
505.814.1413 x 1
marc@mintzit.com
Additional reading:

As reported in the Electronic Frontier Foundation May 9, 2018 article, the U.S. Court of Appeals for the Fourth Circuit ruled today that forensic searches of electronic devices by border agents without any suspicion that the traveler has committed a crime violate the U.S. Constitution (emphasis mine).
This ruling only applies to forensic, not manual, searches of electronic devices at the border.
The legal ruling of U.S. v. Kolsuz (4th Cir. 2018) may be found in its entirety here.

We at MintzIT believe the path to serving you best, includes continuous self-improvement. This is our latest certification. We are the first, and currently only IT consultancy in New Mexico to have successfully passed this certificate.

We at MintzIT believe the path to serving you best, includes continuous self-improvement. This is our latest certification. We are the first, and currently only IT consultancy in New Mexico to have successfully passed this certificate.
We at MintzIT believe the path to serving you best, includes continuous self-improvement. This is our latest certification. We are the first IT consultancy in New Mexico to have successfully passed this course .
.

We at MintzIT believe the path to serving you best, includes continuous self-improvement. This is our latest certification. We are the first, and currently only IT consultancy in New Mexico to have successfully passed this certificate.

We at MintzIT believe the path to serving you best, includes continuous self-improvement. This is our latest certification. We are the first, and currently only IT consultancy in New Mexico to have successfully passed this certificate.

A: The great thing about standards is there are so many to choose from 😉
The industry-standard that most businesses and individuals can pay attention to is the NIST SP-800-171. This details IT security standards for non-federal organizations. This is what federal contractors, health-care providers, law firms, and pretty much everyone else can use to meet compliance.
This document contains over 100 line items regarding IT security, and I won’t attempt to put you to sleep repeating all of them here. The ones relevant to passwords include: