
by Marc Mintz | Sep 20, 2017
Q: HOW TO COLLABORATE SECURELY USING IPHONE OR ANDROID
The easy answer is to use Google Drive with Google Docs (doc, sheet, etc.) Google maintains encryption in transit and at rest, and multiple users can work on the same document at the same time.
Original Post: https://www.quora.com/Is-there-a-simple-program-or-website-that-will-allow-me-to-collaborate-encrypted-documents-with-others-that-are-using-iPhone-or-Android/answer/Marc-Mintz-4

by Marc Mintz | Sep 17, 2017
PRACTICAL PARANOIA MACOS SECURITY ESSENTIALS (ALL VERSIONS) UPDATE: INTERNET ACTIVITY & SOCIAL MEDIA
There have been very significant recent changes in the VPN field, as well as how Facebook and LinkedIn work to help ensure your security and privacy. Practical Paranoia macOS 10.13 Security Essentials (released 9/18/2017) has been fully updated to reflect these changes.
If you are using earlier versions of the book, you may download the updated chapters here.
Practical Paranoia macOS 10.13 Internet Activity & Social Media v1 201709017
![workshops and training]()
by Marc Mintz | Sep 16, 2017
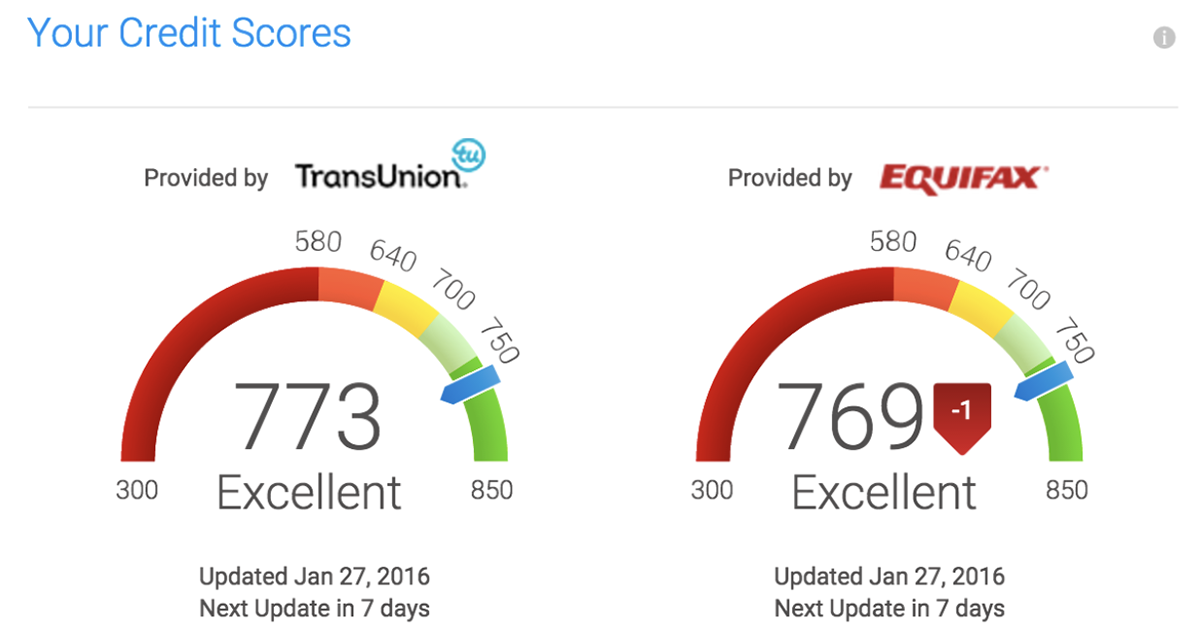
CREDIT KARMA TO LAUNCH FREE ID MONITORING
Reuters announced on 20170915 (https://www.reuters.com/article/us-equifax-cyber-creditkarma/credit-karma-to-launch-free-id-monitoring-following-equifax-hack-idUSKCN1BQ2CJ) that in light of the Equifax fiasco, they are accelerating a new service to provide free identity monitoring. This service will now be available in October 2017.
Credit Karma is one of the largest credit monitoring services. Together with the new identity monitoring, it provides an excellent option to continuously track the two areas likely to be compromised – for free.
To sign up for the free Credit Karma credit monitoring, and to be notified of the free identity monitoring service, visit https://www.creditkarma.com/.


by Marc Mintz | Sep 15, 2017
HOW TO DESTROY A COMPANY THE EQUIFAX WAY
As reported in MarketWatch 20170915 (https://secure.marketwatch.com/story/equifax-ceo-hired-a-music-major-as-the-companys-chief-security-officer-2017-09-15), Equifax CEO Richard Smith was responsible for hiring Susan Mauldin as the company Chief Security Officer.
But just 60 seconds of research finds that Ms. Mauldin has no education credentials in the technology or cybersecurity fields. Instead, she holds BA and MA in music composition. These are fine educational backgrounds for creative positions. But perhaps not so fine when the identity and credit of every US citizen is dependent on the responsible management of technology and cybersecurity.
Since this revelation, Ms. Mauldin’s LinkedIn page (https://www.linkedin.com/in/susan-m-93069a/) has been changed so her name is simply Susan M., holding a position of Professional at Private. Looking further down her page we do see that it still lists her position as Chief Security Officer Equifax.

Susan Mauldin LinkedIn page
What Is The Point, Marc?
Would you choose an auto mechanic to perform heart surgery? Would you choose a heart surgeon to tune up your race car? Few of us can be excellent in even one area of life, fewer still can be very good in two areas.
In the coming months, there are sure to be many revelations of where Equifax made painfully poor business decisions. Hiring a skilled musician to fill the role of Chief Security Officer in an organization with the lives of every American at risk? This may meet the qualifications for criminal activity.
While We Are On The Topic
Who is leading security and technology within your organization? What is their educational background? What industry-standard credentials do they hold? How many years of successful experience in the field do they have?

by Marc Mintz | Sep 15, 2017
ONE MORE REASON WHY YOU MUST HAVE ANDROID ANTI-VIRUS
As reported by Check Point 20170914 <https://blog.checkpoint.com/2017/09/14/expensivewall-dangerous-packed-malware-google-play-will-hit-wallet/>, they have recently discovered at least 50 apps on Google Play that are malicious. These apps have been downloaded on up to 4.2 million Android mobile devices before taken down from Google Play.
This malware has been dubbed ExpensiveWall. It is a variation on a malware found earlier this year on Google. In total, up to 21 million systems have been compromised by this family.
The malware registers the victim to premium services without notification and sends fraudulent premium SMS messages. All of this is charged to their accounts.
How to Protect Your Android Mobile Device
It is vital that every Android mobile device is protected with a quality, independently-tested anti-virus utility. Our current recommendation is Bitdefender <https://play.google.com/store/apps/details?id=com.bitdefender.security>, available from Google Play.
To protect the business network from data harvesting by compromised devices, personal mobile devices should never be attached to the company network. Instead, set up a secondary (or Guest) network for these devices to work on. As the Guest wi-fi is separated from the company network, no damage can occur.
Malicious Apps
The following are the apps known to contain this malware. If these are found on your Android mobile device, they should be immediately removed:
- I Love Filter
- Tool Box Pro
- X WALLPAPER
- Horoscope
- X Wallpaper Pro
- Beautiful Camera
- Color Camera
- Love Photo
- Tide Camera
- Charming Camera
- Horoscope
- DIY Your Scope
- Ringtone
- Safe Locker
- Wifi Booster
- Cool Desktop
- Useful Cube
- Tool Box Pro
- useful Desktop
- Horoscope2.0
- Yes Star
- Shiny Camera
- Simple Camera
- Smiling Camera
- Universal Camera
- Amazing Toolbox
- Easy Capture
- Memory Doctor
- Tool Box Pro
- Reborn Beauty
- Joy Photo
- Fancy Camera
- Amazing Photo
- Amazing Camera
- Super Wallpaper
- DD Player
- Fascinating Camera
- Universal Camera
- Cream Camera
- Looking Camera
- DD Weather
- Global Weather
- Love Fitness
- Pretty Pictures
- Cool Wallpapers
- Beauty Camera
- Love Locker
- Real Star
- Magic Camera
- Wonder Camera
- Funny Camera
- Easy Camera
- Smart Keyboard
- Travel Camera
- Photo Warp
- Lovely Wallpaper
- Lattice Camera
- Quick Charger
- Up Camera
- Photo Power
- HDwallpaper
- Wonderful Games
- BL File Manager
- Wallpapers HD
- Beautiful Video-Edit your Memory
- Wonderful Cam
- Useful Cube
- Ringtone
- Exciting Games
- Replica Adventure
- GG Player
- Love Camera
- Oneshot Beautify
- Pretty Camera
- CuteCamera
- CartoonCamera-stylish, clean
- Art Camera
- Amazing Video
- Fine Photo
- Infinity Safe
- Magical Horoscope
- Toolbox
- Cute Belle
- CartoonWallpaper
- Best Camera
- Colorful Locker
- Light Keyboard
- Safe Privacy
- Enjoy Wallpaper
- File manager
- Fancy Locker
- Cute Puzzle
- smile Keyboard
- Vitality Camera
- Sec Transfer
- Lock Now
- Magic Filter
- Funny Video
- Amazing Gamebox
- Super Locker
- Music Player

by Marc Mintz | Sep 14, 2017
BLOCK WEB TRACKERS WITH GHOSTERY
One of the more malevolent issues with cyber security and privacy is web tracking. There are thousands of businesses whose only job is to monitor everything that you do on the web. With this massive dossier on almost everyone who connects to the web, advertisers, governments, and criminals can know more about you than your mother does.
Although there are several ways to avoid or block such tracking, the easiest and fastest option is by simply installing a browser extension/plug-in called Ghostery (https://www.ghostery.com). With Ghostery installed, you will immediately see who is tracking you, and more importantly, have the tools to block this tracking.
The next release of Practical Paranoia Security Essentials will include a section on Ghostery. A copy of the section is available here.
Practical Paranoia Ghostery

by Marc Mintz | Sep 13, 2017
TPP Is All About Making Your STEM Course Its Best
Cybersecurity is everyone’s business. And nobody is going to be able to ensure your data, identity, and credit security more than you.
This is why the Practical Paranoia Security Essentials (PPSE) courses and workbooks have become the #1 choice for DIY and STEM cybersecurity classes. Each book is a comprehensive course, written for the non-technical computer user, but covering everything a computer professional expects on the topic. GUARANTEED to be the easiest and most-comprehensive books in their category.
PPSE books are available in Kindle, paperback, and now Live online editions. When purchasing your books for class, teachers get free exams, desk copy, PowerPoint presentations, and telephone support from the authors. No other publisher gives you more to ensure the best possible course.
For more information, or to order your books, visit https://thepracticalparanoid.com, or call (888) 504-5591.

by Marc Mintz | Sep 13, 2017
Q: Are all iMessages encrypted end-to-end, on every phone provider plan?
A: If sending from iMessage to iMessage, it is encrypted point to point. However, Apple holds a master key, and is able to read all iMessages.
It was recently reported that Apple does archive iMessages for between 1–3 months.
For true point to point encrypted messaging, without a middleman able to recover your messages, I recommend wire.com.

by Marc Mintz | Sep 13, 2017
Q: How can I know everything about computer security?
A: The first step to wisdom is recognizing one doesn’t know much of anything.
In the case of Technology, new information is generated geometrically faster than a human can absorb it – even if that is their full-time job. And if you are in Cybersecurity, you already have a full-time job earning a living!
So while desiring to know everything about the topic is an admirable goal, it can never be realized.
If you wish to become an expert in the field, there are some steps you may wish to take:
- Earn a BS in computer Science
- Earn a MS in Computer science with a specialty in cyber security.
- Earn your way through the industry certifications – CASP, CEH, etc. the secondary advantage of earning the degree and certs is that it allows you to get close to others who are leaders in the industry, and to share knowledge with them.
- Attend security conferences such as Blackhat where you can learn from experts before the info is even published.
- Teach. It’s astounding how much you have to learn when asked questions by students.
- Be humble. I doubt any of us know even 0.1% of what is already known in our field. Be open to change perspective, opinion, and stance on a dime when the evidence points in a different direction.
Original Post: https://www.quora.com/How-can-I-know-everything-about-computer-security/answer/Marc-Mintz-4

by Marc Mintz | Sep 13, 2017
Q: Can the retails shops or any store retrieve our email ID’s with the help of credit card details (I never gave my email address but they send me invoices/receipts to my email address)?
A: Of course! Not that the stores themselves can directly make the connection between your credit card and email address, but there are many companies out there whose sole purpose is to connect the dots from scraps of data to come up with a comprehensive inventory for all that makes you, you.
And this includes your email address, the websites you visit, which ads you click, how much time you spent on each web page, who your friends are, where you use your credit cards, your income, your sexual preferences, you name it.
Install Ghostery on your browser to see all the companies that are tracking you, and block those buggers.
Original Post: https://www.quora.com/Can-the-retails-shops-or-any-store-retrieve-our-email-IDs-with-the-help-of-credit-card-details-I-never-gave-my-email-address-but-they-send-me-invoices-receipts-to-my-email-address/answer/Marc-Mintz-4

by Marc Mintz | Sep 13, 2017
Q: Do we need to use separate VPN services in 1 household?
A: This depends on your preferences, and on the end user license agreement with the VPN services.
If everyone in the household that wants to use the vpn agree on the same service, and that vpn host allows X number of devices to be used, All is good.
But if one person prefers one provider, and another prefers a different provider, or if you have 5 people in the household, but the provider only allows 3 devices, you may need multiple providers.
A possible solution is to choose a provider that is compatible with using their vpn on a router. Once you’ve configured the router for their vpn service, every device in the household gets vpn coverage, and it counts as only one device.

by Marc Mintz | Sep 13, 2017
Q: Are my files safe on Cloud storage, or should I encrypt them before I upload them?
A: The files are safe from most criminals, and internal corporate spy’s.
But not safe from from the cloud support staff, nor government troublemakers. All these folks have keys to read your data.
To block everyone, you need to aes256 encrypt individual files or folders with something like veracrypt (https://www.veracrypt.fr/en/Home.html) or Virtru (https://virtru.com).
Original post https://www.quora.com/Are-my-files-safe-on-OneDrive-or-should-I-encrypt-them-before-I-upload-them/answer/Marc-Mintz-4

by Marc Mintz | Sep 13, 2017
NEXT STEPS TO AVOID IDENTITY THEFT
Last week it was revealed that most of the US adult population has had all necessary data stolen from Equifax to make it easy for criminals to steal their identity, take out mortgages, car loans, and get new credit cards in their name.
Recovering from identity theft is an expensive, and 1-2 year process. It is vital to get in front of this issue before it tramples most of us.
Theft Areas
The most common areas of identity theft include:
- Child ID theft. This level of theft can exist for a decade or more without notice. Once the child becomes an adult, the damage is done and very difficult to recover from.
- Credit ID theft. The criminal uses your identity to apply for and get new loans and credit cards.
- Tax ID theft. The criminal uses your social security number to file tax returns, of course using their address to send refunds.
- Medical ID theft. The criminal uses you identity to get medical services, or to push fraudulent billing.
- Social ID theft. The criminal uses your identity information to create fake accounts on social media.
Steps To Take Now
Every person should take the following steps to help prevent identity and credit theft:
- Social Security Number. There are very few instances where your SSN is required. Instead, offer only the last 4 digits. Don’t carry your card.
- Keep identity data private. When asked for personal identity data (full name, birthdate, bank account, etc.) by unsolicited sources, keep quiet.
- Freeze your credit reports. Contact Equifax, TransUnion, Experian, and request a freeze on your credit reports. This prevents anyone from applying for credit in your name.
- Secure your mobile devices. All of your mobile devices should have a password, hardware encryption, and erase after 10 failed password attempts. Millions of mobile devices are stolen annually, and each holds the keys to your financial and identity kingdom.
- Only use a public wi-fi network when using Virtual Private Network (VPN). I personally recommend always using a VPN, even when on your own network.
- Review your credit card and bank statements monthly for unauthorized transactions.
- Purchase and use a micro-cut paper shredder for all documents to be trashed that contain financial or personal data. Micro-cut is important to prevent dumpster divers from piecing together the paper jigsaw puzzle.
- Store documents with financial and personal information in a safe.
- Secure your computers. This includes a professional security audit. It is not enough to just install antivirus and a firewall.
- Use strong passwords (minimum 15 characters).
- Use different passwords for each site.
- Review your credit report at least yearly. This can be ordered from http://anualcreditreport.com.
Reporting Theft
Should you find that your identity or credit has been stolen:
Need More Information?

by Marc Mintz | Sep 13, 2017
EQUIFAX HACKED AGAIN!
As reported in the BBC on September 13, 2017 noon mt (http://www.bbc.com/news/technology-41257576), Equifax Argentina has been breached.
It appears that an online employee tool could be accessed using the default administrator credentials of Username: admin, Password: admin.
Really?!
Equifax spokesperson stated they immediately shut off access to the site as soon as this vulnerability was discovered.
Included in the breach are Equifax Argentina employee information, and 14,000 records of Argentinian complaints/disputes with Equifax, including the person’s name, and DNI (equivalent to the US social security number).

by Marc Mintz | Sep 12, 2017
Business Continuity and Disaster Recovery
You Back Up Your Data. Do You Have a Backup for Your Computer?
You need to back up your computer. Now, if you have not already.
Most folks reading this blog know that it is not a matter of if you will lose data, only a matter of when, how often, and how freaking horrible will it be.
That’s why everyone reading this has at least two data backups: at least one full on-site backup and at least one off-site (or internet) backup.
But let’s look at this from the perspective of losing as little productive time as possible. This falls under Business Continuity and Disaster Recovery.
If you are like me and can’t function without glasses, you have a second (or third) pair of glasses hanging around. Because you know without clear vision, you are down for the count. If you are a woodworker, you have more than one chisel. A cowboy has more than one horse. A race car driver has a spare of everything for his car.
So. If your job is dependent on a functional computer, what happens when the motherboard gives up the ghost? Or a drive goes bad? One day, that will happen. The average life of these with daily use is around 3 years.
Sure, you have your data backed up, but how long will it take for you to get fully functional?
- First, you must locate a compatible computer.
- Then, the replacement computer needs to have all needed applications and updates installed.
- By the time your data is copied over to the replacement machine, it may be a day or two before you are back in business.
And how much will this downtime cost you and your business? A simple web search found such a broad range of loss calculations –- from $1,000-$3,000,000/hr – isn’t useful.
But let’s do a bit of mind experiment. If employee A is sitting on hands for a day because of IT downtime, that means the widgets A was to produce for employee B to perform a value-added task weren’t going to B, so B also is sitting on hands. And of course, the work that B was to do to hand off to employee C? Well, you get the picture. There’s a whole lot of hands being sat on just because of one down system.
Now consider the cost per employee, and this starts to look like real money!
We haven’t even looked at how customer satisfaction is impacted because widgets are now in short supply, or the register lines are painfully long.
If you are a one-person shop? Your business just went from 100% productivity and sales to 0% in a nanosecond.
The Solution
Your solution is no different than my need for glasses, the woodworker’s need for multiple chisels, the cowboy’s need for a few horses, and the race car driver’s warehouse full of spare tires, windows, fireproof suits and lug nuts.
If your job is dependent on a computer, you simply must have a spare hanging around.
In my case, I have a new $3,600 rocket ship for my primary computer. But my spare is a beat-up, three-year old that runs at around 1/8th speed. But it lets me do my job in an emergency.
In other words, I can maintain business continuity. And I can recover almost immediately from a disaster because I planned for this possibility.
The Strategy
It is vital that you get back to doing your work. If you already have a spare computer, you have saved yourself at least a day of shopping and computer setup.
The next longest delay is loading your data from backup to computer. It’s so old-school to store data on a computer, I don’t do this at all.
Instead, for better productivity, continuity, and security, data should be stored on the web with a Cloud service. This solves several problems:
- Should you be away from your computer – perhaps on the other side of the planet – as long as you have a browser, you can access your web-based data using your mobile phone or another computer.
- If your computer is stolen, all they get is a computer. Your data is stored, encrypted, on a Cloud service.
- A large piece of your Disaster Recovery plan is taken care of. Should catastrophe strike (think Texas or Florida), you and your staff can get right back to business from hotel rooms in another state.
- And when your computer fails, you are back in business within 15 minutes with the following steps:
- Place the dead computer in a corner for service.
- Move the spare onto your desk.
- Power on, log in.
- Launch a browser.
- Enter your password.
- All your data is there!
The Specifics
Business continuity starts with acquiring a backup computer. As this is just an insurance policy to get you through until your primary computer is repaired or replaced, the backup doesn’t need the same high-end specifications as your primary machine. It just needs to be “good enough.” I recommend a minimum of 8GB RAM, 120GB storage (SSD if possible), and Intel i5 dual-core CPU.
Just like your primary computer, the backup computer should be kept up-to-date. This means monthly system, application, and security updates. If these aren’t done, there may be hours of updates to complete before the spare can be used in an emergency. Worse, any virus not neutralized on the spare can render it useless.
This process revolves around using Cloud-based file services to store your documents instead of storing them on your local computer. There are over a hundred Cloud file server vendors. Microsoft, Google, and DropBox are best known. Determine which is best for you by comparing how they meet your needs. I use Google. My reasons are:
- Cost is low.
- Starts at $5/month/user, up to $25/month/user for enterprise services.
- Data is encrypted in transit (between their servers and your computer).
- Data is encrypted at rest (on their servers).
- Google security meets HIPAA and SEC security requirements.
- If you are in a medical or financial job, you should know these terms.
- Email service is world-class.
- Setup is very simple.
- Telephone support 24/7.
- Up-time is unmatched.
Google Cloud file service is called Google Drive. It is easy to obtain.
- Once you have a Google account, just download and install the Google Drive application called:
- Backup and Sync for users of the free Gmail.
- File Stream for users of G-Suite.
- With either of these products installed, you will find a new folder at the root level of your home folder named Google Drive.
- Anything you place in this folder is synchronized with the Google server. So, your file changes automatically are maintained.
- Configure a folder hierarchy within the Google Drive folder to match your workflow, and then move all your documents into Google Drive.
This initial setup will take from 15-30 minutes (not counting time for Google to synchronize).
Once synchronized, should your computer be swallowed by a black hole, just follow steps 1-5 above, and get back to making money!


by Marc Mintz | Aug 28, 2017
CYBERSECURITY: DOES IT MATTER?

UNM presents a special opportunity to learn how to make your business smarter and more secure. The intelligent use of technology can be a defining point between those who succeed in business, and those who fail. Think Henry Ford, Thomas Edison, Steve Jobs… You too can be a leader who intelligently uses technology to gain a competitive advantage. And you can protect that advantage through defensive Information Technology (IT) practices. Come see how essential methods and tools will make your business more successful.
Spend an evening with UNM cybersecurity experts for this fascinating panel discussion. Featuring Marc L. Mintz (author of the #1 best-selling Practical Paranoia Security Essentials book series) and Glenn Norman (Certified Ethical Hacker).
- When: Wednesday, September 6, 2017, 6pm-8pm
- Where: UNM Continuing Education South Building, room 207
1634 University Blvd NE, Albuquerque, NM 87102
- Why: The success of your business, the security of your information, the privacy of your family
- What to Bring: Curiosity and questions
- Cost: Free
Call 505.277.0077 to register for CyberSecurity: Does it Matter? Infobyte ID: 82132


by Marc Mintz | Aug 23, 2017
A: A usb Drive is just a storage device. Connecting it to a computer doesn’t do anything to provide remote access or control.
If the usb Drive has remote control software in it, you connect the drive to a computer, install the software, and have the corresponding control software in your computer, then you will have remote access and control.
There may be over 100 applications that can provide this function. I’m particularly fond of LogMeIn Hamachi.
(Originally published on Quora.com https://www.quora.com/If-I-plug-in-a-USB-drive-in-another-computer-can-I-make-it-so-I-can-remote-control-that-computer-at-home)

by Marc Mintz | Aug 22, 2017
PRACTICAL PARANOIA SECURITY ESSENTIALS WORKSHOPS AT UNM CONTINUING EDUCATION
You don’t need to be a Microsoft Engineer, Apple Genius, or Google Guru to know state-sponsored system penetration, ransomware, malware, hackers, pranksters, and even a whackadoodle ex or two are out there to get you. You includes your data, intellectual property, financial information, personal communications, web activity, Amazon, bank, and credit card credentials, and more. Now is the time to take back control over your Android, iOS device, macOS, and Windows computer security. In this 24-hour course, any user, from novice to IT professional, will discover their IT vulnerabilities, and then implement the same easy and simple strategies used by the NSA and military to defend against attack.
The Practical Paranoia Security Essentials Workbooks have been the best-selling, the highest- rated, and most comprehensive workbook available for any platform. Bring your mobile device or computer to these workshops, and then leave with hardened security. All workshops are taught by cyber security professionals and authors of the Practical Paranoia Security Essentials course manuals.
Did we mention that the workshop pricing is offered at 50% discount for this time only?
REGISTER
Point your browser to <http://ce.unm.edu/professional/computer/index.php> click Classes, then click Computer Professional, or Call 505.277.0077 to register
All Practical Paranoia Security Essentials workshops are currently offered at $395, and include the full version of the workshop manual ($64.95 value).
- Android 6 Security Essentials, #65134, Dec 1-18, MWF, 6p-9p
- Ethical Hacker, #63135, Jan 9-30, T TH, 8a-12p $995
Registration for this section opens 11/27/17
- iOS 10 Security Essentials, #65133, Sept 27-Oct 13, MW, 2p-5p
https://newmexico.augusoft.net/index.cfm?method=ClassInfo.ClassInformation&int_class_id=82130&utm_source=Computer%20Professional%20&utm_medium=ce-class-list&utm_campaign=iOS%2010%20Security%20Essentials&_ga=2.36655392.1276751975.1502264020-1269314583.1502264020
- macOS 10.12 Security Essentials, #65132, Sep 8-25, MWF, 6p-9p
- Windows 10 security Essentials, #65131, Oct 2-18, MWF, 6p-9p
https://newmexico.augusoft.net/index.cfm?method=ClassInfo.ClassInformation&int_class_id=82125&utm_source=Computer%20Professional%20&utm_medium=ce-class-list&utm_campaign=Windows%2010%20Security%20Essentials&_ga=2.3445168.1276751975.1502264020-1269314583.1502264020

Marc L. Mintz, Author, and course presenter Practical Paranoia Security Essentials Series
“There is simply no other workshop or training that you can attend that will protect your personal and business security as well as Practical Paranoia Security Essentials. Bring your older children, friends, family, co-workers, and boss. Everyone should be responsible for personal and business cyber security. This workshop delivers the same powerful tools as in NSA or NIST trainings, with all technobabble removed. Everyone from a teenager, stay-at-home mom or dad, the office technophobe, as well as the office IT staff will find these 24 hours the best spent in years.”
Still have questions?
Feel free to contact to author & instructor, Marc L. Mintz, 505.814.1413 x 1 or marc@thepracticalparanoid.com.


by Marc Mintz | Aug 22, 2017
SPEND AN EVENING WITH MARC L. MINTZ AT UNM
CYBERSECURITY: DOES IT MATTER?

UNM presents a special opportunity to learn how to make your business smarter and more secure. The intelligent use of technology can be a defining point between those who succeed in business, and those who fail. Think Henry Ford, Thomas Edison, Steve Jobs… You too can be a leader who intelligently uses technology to gain a competitive advantage. And you can protect that advantage through defensive Information Technology (IT) practices. Come see how essential methods and tools will make your business more successful.
Spend an evening with UNM cybersecurity experts for this fascinating panel discussion. Featuring Marc L. Mintz (author of the #1 best-selling Practical Paranoia Security Essentials book series) and Glenn Norman (Certified Ethical Hacker).
- When: Wednesday, September 6, 2017, 6pm-8pm
- Where: UNM Continuing Education South Building, room 207
1634 University Blvd NE, Albuquerque, NM 87102
- Why: The success of your business, the security of your information, the privacy of your family
- What to Bring: Curiosity and questions
- Cost: Free
Call 505.277.0077 to register for CyberSecurity: Does it Matter? Infobyte ID: 82132

by Marc Mintz | Jul 6, 2017
Q: How can you get WiFi without internet?
Absolutely!
A WiFi router, hot spot, or other device that provides a Wi-Fi signal for other devices to connect with, will do just that without an Internet connection. This can be done to create an ad-hoc local network for multiple people to play computer games or share data with each other. The only thing missing would be the ability to get on the Internet.
Technically, a Wi-Fi router is defined as:
- Created a wireless network allowing X devices to communicate with each other
- If an Internet connection is available, will link the two different networks (Wi-Fi and Internet) together, so that (baring firewall or other blockages) Internet activity can reach the users of the Wi-Fi network, and the users of the Wi-Fi network can reach the Internet.
Original post- https://www.quora.com/How-can-you-get-WiFi-without-internet





























