New Credit Card Fraud Operating in the Wild
Just when you thought it was safe to go back into the water.
Oh, wait. Wrong movie!
Do you have a credit card? Do you have a cell phone? Of course you do! And if a bad actor gains access to both of these, they have found an effortless way to gain full control over your credit card account.
The Hack
This hack was discovered when the bad actor was caught in the act at in the locker room of a gym. The process works like this:
- The bad actor (BA) opens lockers (at least at the gym) to gain physical access to then victims phone a credit card.
- BA uses their phone to attempt log in to your credit card account, tapping the “Forgot my password” or “Reset my password” button.
- An authorization code is sent to the victims cell phone.
- IF (big if) the victim has configured their phone to display messages while in Lock Screen mode, the authorization code is clearly visible to BA.
- BA enters the authorization code on their phone. This gives BA the opportunity to change your password, phone number, email address, and all other vital information.
- At this point, BA has full control over victims credit card account.
The Fix
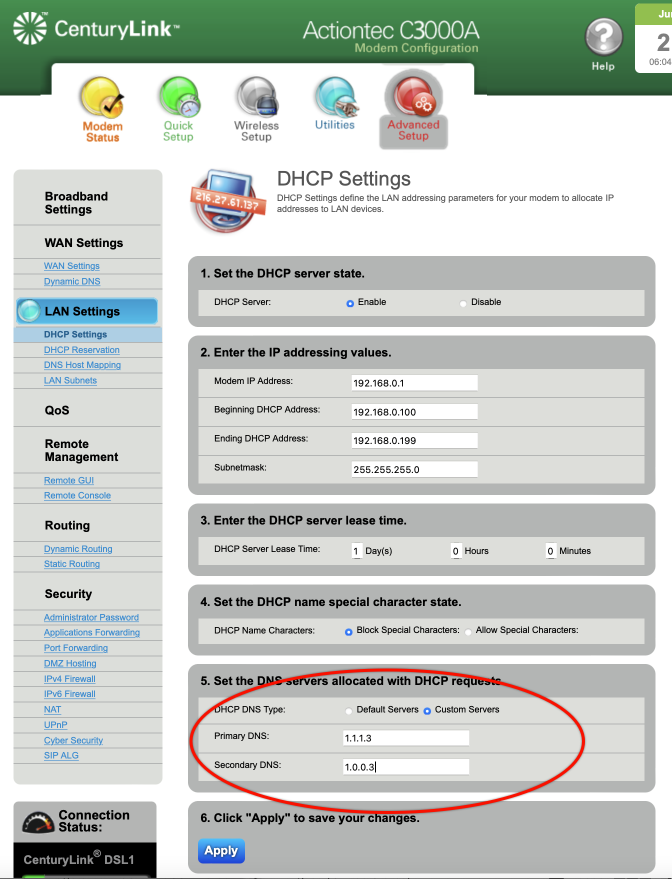
Fortunately, the fix is straightforward and simple. All that need be done is to prevent messages from displaying on your Lock Screen. If you have followed me for any time, you know I’m a fan of not allowing ANYTHING to display on the Lock Screen.
For those of you who have just upgraded to iOS 16, this can be done from Settings > Notifications > Messages > disable the Lock Screen option. It is OK to leave Notification Center and Banner notification enabled.
For Android users, open Settings > Privacy > Notifications on Lock Screen > enable Don’t show notifications at all.
50% DISCOUNT ON ALL PRACTICAL PARANOIA BOOKS
IOS 16 AND IPAD 16 ARE NOW AVAILABLE
And so are the vulnerabilities to your device, data, and communications!
iOS 16 is the MUST HAVE upgrade for your iPhone and iPad. In addition to dozens of new features, iOS 16 has dramatically improved the options for your cybersecurity and internet privacy.
But you need to know HOW to properly configure your device to ensure your security.
Practical Paranoia Security Essentials has been doing just that for over 8 years at the best-selling, easiest, most comprehensive guid to securing data and communications on your home and office devices.
And from now until September 30, 2022, ALL Practical Paranoia Live! Edition books are 50% off!
Visit https://thepracticalparanoid.com to order at half price today. Just enter discount code “50” at check-out.
All Practical Paranoia Security Essentials books are available in paperback, kindle, and Live! editions.
Live! editions are exact replicas of the paperback and kindle editions, made available through Google Drive. This is the version used by Universities, trade schools, and high schools, and is now available to everyone. Its advantages include: Always available on any device with a browser and internet connection, and automatically and constantly updated as the OS, applications, and best practices evolve.
Questions, call +1.505.453.0479