Secure ALL Your Internet of Things with VPN
Unless you have been living in an ice cave the past few years, you are sure to have heard the term “IoT” or “Internet of Things”. Given all the catastrophes each of us has had to deal with, you would be excused if you haven’t given this topic your attention. After all, we have been in survival mode.
Now that the election is over and you’ve gotten your shots, maybe you can take a few minutes to learn why IoT is vital to your cybersecurity and internet privacy.
What Is IoT?
The Internet of Things (IoT) is anything and everything that has an embedded sensor, software, or other technology for the purpose of connecting and exchanging data with other devices and systems over the internet.
Although you may not know it, you probably have a lot of IoT in your home and office. Items like:
- Medical equipment (think heart monitors, CPAP machines, even the Help! I’ve fallen and can’t get up alerts.
- Home automation, perhaps a water leak detector, smart thermostat, remote control lighting.
- Smartwatch
- iPhone or Android phone
- Amazon Echo, Google Home, Apple HomePod, Samsung SmartThings Hub
… And Why Should I Care?
If you are like me, you may be just about cared-out by now. Between politics, climate collapse, pandemics, and discovering a few of my relatives are bat $#!* crazy, it’s getting more difficult by the day to care about new things.
But – you have to trust me on this – giving just a bit of thought to IoT is going to save you an armload of grief down the road.
Why?
Because even though you may do your best to secure your computers and mobile devices to help ensure your cybersecurity and internet privacy, few people give thought to securing their IoT. I mean, it’s only a doorbell (or thermostat, or voice-controlled TV, or, or, or…)
All these out-of-sight, out-of-mind devices are connected to your network. And if a criminal gains access to an IoT device, they gain access to your network, and may be able to view all of the data that travels through it – including usernames and passwords – and therefore have access to the keys to your kingdom.
Criminals are focusing attention on your IoT devices because they are often far easier to penetrate than servers, computers, and mobile devices. In fact, many of the older IoT devices (when it comes to technology, older may mean three years old) have no functional security at all!
Give Me an Example
How about:
- A casino experienced a major data breach when criminals gained access to the network through a smart thermostat used in an aquarium.
- A United Airlines flight was commandeered by a passenger who hacked the flight control system through the entertainment system.
- Smart toasters were remotely hacked so they wouldn’t toast any bread the hacker considered unhealthy.
- Freezers were remotely hacked to automatically shut down when ice cream was detected.
- The Mirai malware takes over IoT devices such as cameras and monitors, turning the device into a bot.
- A car was remotely hacked over the internet giving the hacker full access to the A/C, steering, and turning the engine off.
- The FDA recalled almost 500,000 pacemakers over fears they could be remotely hacked.
As I’ve said far too often, the list goes on and on, but we both have a life to lead.
But What Can I Do About It?
PLENTY! In fact, so much that I’m writing a book on the subject.
But until that is released, one of the most important things you can do is to connect your IoT devices to the internet via a Virtual Private Network (VPN).
If you have been following me, you already know I think your computer, phone, and tablet should always and only connect to the internet via VPN. This encrypts data between your device and the internet.
Few people do the same for their IoT devices. But that is no different than locking the front door as you leave for vacation, but leaving the backdoor open.
Very few IoT devices have the ability to do VPN by themselves. No worries! You can configure your router to do the work for you.
Some Background on VPN for Routers
Not all routers have the ability to work with VPN. So if yours cannot, it is definitely time to replace it. Routers are a relatively low-cost item, and certainly far less costly than a data breach. Think draining your bank account, identity theft, someone buying a home using your ID, unauthorized credit card charges, and more.
I’m fond of ASUS routers. They are a high-quality prosumer product. For my example, I’m using their latest & greatest router, the GT-AXE11000. But they have several less expensive models that work exactly the same.
What needs to be done to secure your home and office IoT is to enable VPN on your router, then configure the router to connect your target devices to that VPN. In the case of my router, I can create up to 16 different concurrent VPN configurations, allowing me to balance security, performance, and apparent geo-location on a device-by-device basis.
Prerequisites:
- A VPN account. There are literally thousands of VPN providers available. Most of them throw red flags for me. Many are criminals. I recommend NordVPN. Reasonable cost, allows multiple devices, consistently ethical, and they provide detailed instructions how to configure many routers to work with their service.
- A router that can be configured to work with your VPN provider.
Step-By-Step Configure a Router For VPN
- Get a VPN account. For this example, I’m using NordVPN.
- Get a router that can be configured to work with your VPN provider. for this example, I’m using the ASUS GT-AXE11000.
- Open a new browser window to your VPN provider support page. They will have a VPN configuration file to be downloaded for upload to your router. Download the file.
- Connect and log in to the router control panel.
- In the router control panel, select the VPN tab or section. For my router, VPN is selected from the sidebar.
- Select the type of VPN to be used. For my router, the options are VPN Server, VPN Fusion, and Instant Guard. VPN Fusion is what is needed. Most other routers call this VPN Client.
- Scroll down to the Server List area. This is where you configure your various VPN setups.
- Tap the + button to create a new server.
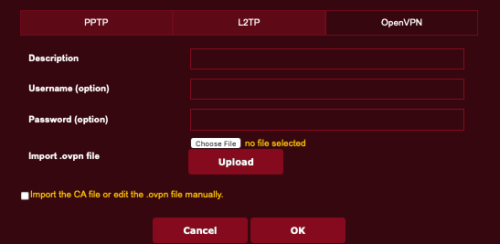
- Tap the VPN protocol you want to use. In most cases this is OpenVPN.
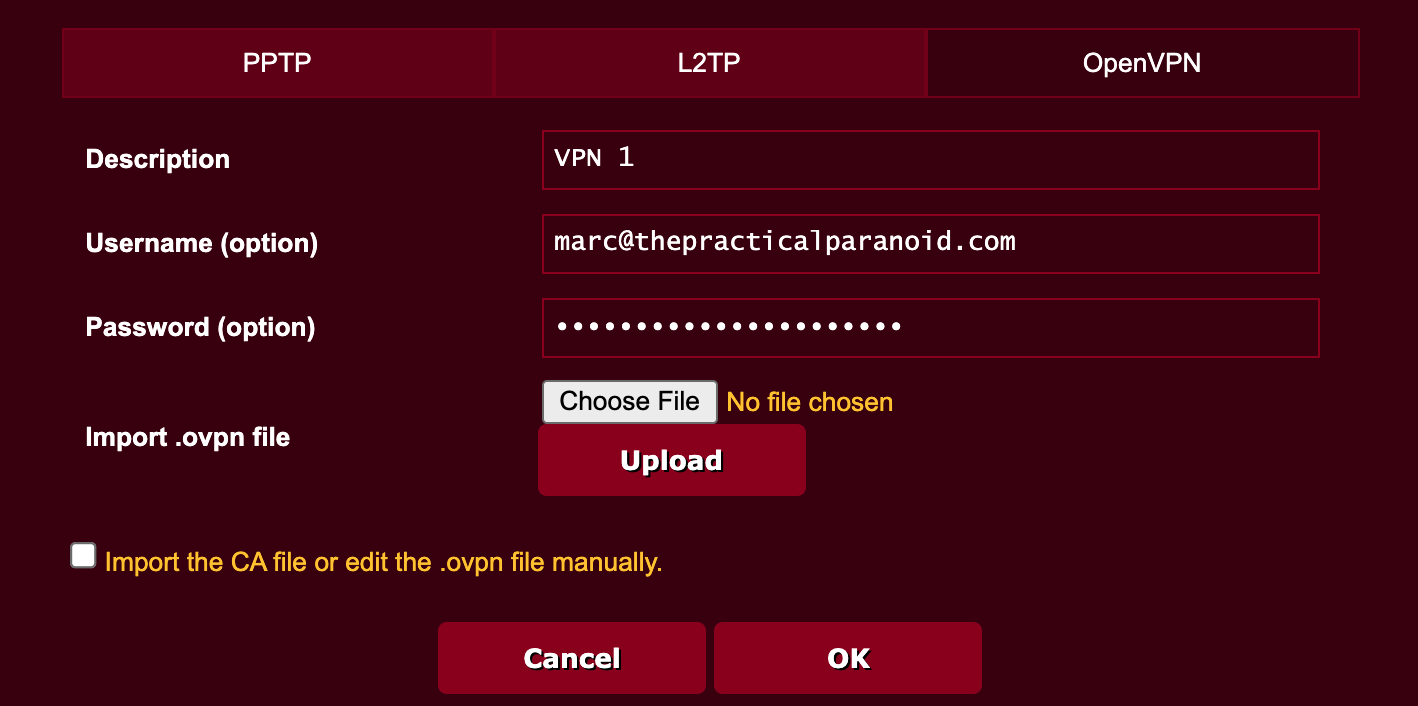
- Enter your VPN account credentials.
- Tap the Choose File button, then navigate to select the VPN configuration file downloaded from your VPN provider earlier in step 3.
- Tap the Upload button to install the VPN configuration file.
- Tap the OK button.
- Back to the router VPN page, you will see your new configuration listed. Tap the Activate button to enable the use of the configuration.
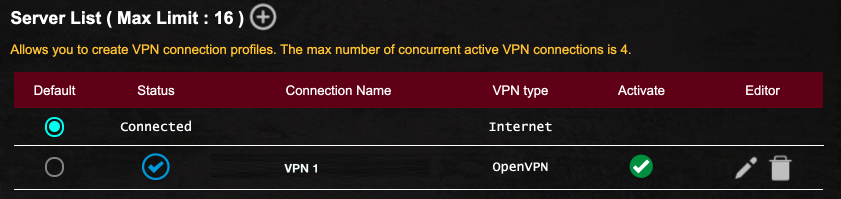
- Scroll down to the Exception List. This is where you assign devices. to use VPN.
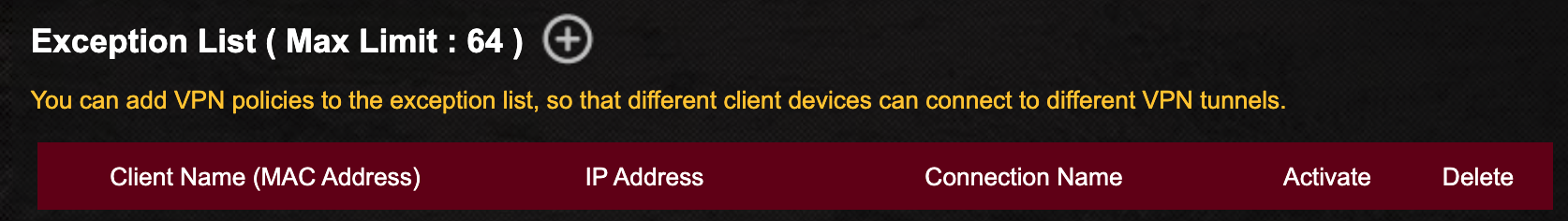
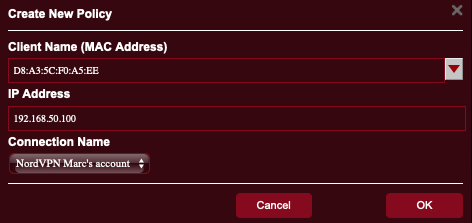
- Tap the + button. The Create a New Policy window opens. From here you select the target device(s).
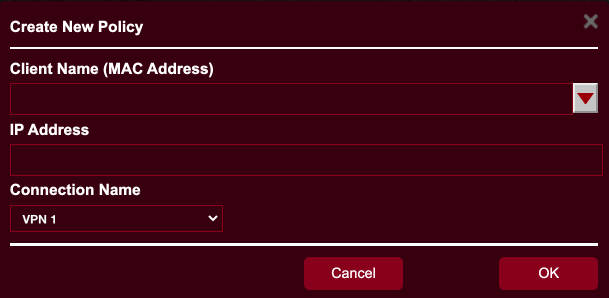
- Tap the Client Name field. A list of all devices currently connected to the router appears. Select your target device. It will show in the Client Name field, and its IP address shows in the IP Address field.
- Tap the Connection Name field, then select the VPN configuration you created earlier.
- Tap OK.
- The device appears in the Exception List.
- Tap the Activate button to enable the device to use VPN.
- If you have additional devices you want to be connected to VPN, repeat steps 16-21.
- Tap the Apply button to save your work.
- The router will save the settings, then reboot.
- Once the router is back online, the target device(s) will be connected via VPN, secure from prying eyes.