
by Marc Mintz | Jan 18, 2023
Why
Many of us know how vital it is to ensure our computers, phones, and software are updated on a regular basis. But very few give the same thought to our routers and modems.
But perhaps I’ve gotten ahead of myself. The big question is “What is all the fuss about updates? After all, I’ve got the features I need”.
There are three reasons developers release updates:
- Monitization. At some point the developer often charges for updates. This is a reality of being in the type of economy we in most developed states.
- Bug fixes and new features. There are always bugs and features to be added.
- Security fixes. Ok, this technically falls under “Bug fixes”, but it is important enough to have its own bullet point. Bullet points are cheap!
Security fixes are my focus for updates.
Security fixes typically result from a breach. Once it has been discovered and the appropriate developer notified, they eventually get around to fixing it. There will always be someone who is the first to be hacked by a vulnerability. But you can certainly avoid being a future victim by installing the security fix.
Back to routers and modems.
The majority of users never check their network equipment for software or firmware updates. It is common for me to see a five year old router that not only has never been updated, but the default administrator, admin password, and wifi password are all still at defaults.
This is understandable. Unlike your computer or phone, updating network equipment is not a one-click operation, and it involves dealing with a device that is alien to all but IT professionals.
But like most everything else in life, it’s easy when you know how.
How
The easiest option is if your network device is leased or was purchased from your ISP–like Xfiniti, Qwest, AT&T, etc. In that case, just give customer support a call and ask them to ensure the device is updated. They can do this remotely, often in under five minutes.
If your device doesn’t fall under this condition, it is still easy. As every device is different, let me outline the process instead of giving device-specific detailed step-by-step instructions:
- As updating a network device will break a network connection temporarily, ensure that nobody and no device is actively working on either the Internet or local network.
- Pull out or download the manual for the device. What you are looking for is the default administrator username and password. If you have changed these, you should already have the. credentials at hand.
- Figure out the IP address of the device. Most network devices have an IP address of 192.168.0.1 or 192.168.1.1. You can find your device address by opening up your network settings or preferences on any device connected to your network. The specific field within the network settings may be called “router” or “gateway”.
- Most network devices can be accessed using a web browser. Open a browser, then instead of entering a website name into the URL or address bar, enter the router IP address, then tap the. Enter or Return key.
- The network device will present an authentication window. Enter the administrator username and password, then tap the Enter button.
- Once into the device, look around for the firmware update area. The manual becomes your friend here.
- Tap the Update button. The download and update typically takes 5 minutes. During this time the device is offline–even to you.
- When the device comes back online, try to update again. Some devices can only update incrementally. I just finished with a device that had to be manually updated 4 times.
- Exit your browser and you are done! See, it really was easy!

by Marc Mintz | Jan 9, 2023
A: First, let us review the problems with traditional passwords.
- The overwhelming majority (perhaps up to 90%) of users use the same password(s) for everything. Although this is great for remembering your passwords (you only have one or two passwords you have to remember), it is terrible for security. In the event one of your sites becomes compromised and your credentials stolen, all the criminal need do is launch a script that will try the same credentials on thousands of other sites. Within a few minutes all of your data – and often savings and credit cards – are owned by someone else.
- For the minority of users that actually do use a variety of passwords, they will almost always use weak passwords which can be cracked in just a few minutes. Although “weak password” definition will vary among system admins, as a broad generality any password with fewer than 15 characters is weak.
- Most users do not use a password manager, making for very insecure storage of passwords. This forces them to write their passwords down. As I’ve been in the industry for over 30 years, I’ve seen it all – including passwords taped to the bottom of keyboards, the password to the server posted above the receptionist station, and even a 3-ring binder with 72 point type on the cover saying “Office Passwords” left out in the open in the waiting room.
So, back to the question of what is more secure than traditional passwords?
- Strong passwords, unique to every site and service, stored as encrypted within a password manager. I’m very fond of Bitwarden and use it as my own password manager. Bitwarden encrypts each password on the device, with an option to synchronize the encrypted database with your other devices. It also serves as a One Time Use Password generator (authenticator). More on that next.
- Use One Time Use Passwords along with your strong password. Most people know these as authenticator codes. When you enter your credentials to a site, you will be prompted for an authenticator code. These are random numeric codes generated every 30 seconds by an authenticator application. Although all sites don’t yet make use of these, all of the major ones do.
- FIDO key. A FIDO key is a device that looks like a thumb drive that you carry on your person. To access a site you must first attach (via USB or Bluetooth) the key to your device. It will provide strong credentials. FIDO keys work great, but haven’t taken the industry by storm and few users are willing to deal with one more piece of equipment they have to carry.
- Biometrics. You’ve used these. Fingerprint scanners, retina scanners, facial scanners, voice recognition scanners. I even watched a presentation to the military for the implementation of a body odor scanner! And while these work great to provide credentials to access your device, they haven’t been integrated for use with many websites to date.
So, what’s a conscious technology user to do? My recommendation is to stick with strong passwords, using a different one for every site and service. Use your credentials along with a quality password manager and one-time-use-passwords.


by Marc Mintz | Jan 7, 2023
Although many people have jumped onto the cryptocurrency bandwagon, only a few actually understand how crypto works (and I’m using the term “works” very loosely).
My personal take from day one has been that crypto is the second grandest-scale hoodwinking in the history of humankind. A judge, Martin Glenn, in the legal case of crypto lender Celsius Network has redefined outrageous behavior by declaring that the monies deposited by investors in Celsius does not belong to the investors. Instead, it belongs to Celsius!
In terms that we can all understand, this means that for the 500,000 people who invested in Celsius, they simply gave their money to Celsius and will now get nothing in return!
Unfortunately, this ruling is based on the terms specified in the lengthy contract an investor signs when joining Celsius. Worse yet, it appears these same terms are used in many other contracts within the financial community. Which begs the question: When was the last time you took the time to fully review a contract of import that you were to sign?

by Marc Mintz | Dec 30, 2022
Answer:
Were you my client, my first question would be “how do you know?” Because under normal conditions, there is no need to know an employee password.
But no matter how you were to answer my question, the answer is to assign a Password Policy to the computer. Heck, while you are at it, assign a Password Policy to all company computers.
A Password Policy can be applied to Chrome OS, macOS and Windows computers. The process is a bit involved to give a detailed description here on Quora, but an internet search will provide you with the step-by-step.
With a Password Policy, you can specify a minimum number of characters, minimum complexity (upper case, lower case, numbers, and special characters), password lifespan, and prohibit the reuse of previous passwords.
Or, you could be the brightest one in the room and read one of my Practical Paranoia Security Essentials books, which do provide the illustrated step-by-step instructions.
You may also consider including a password policy compliance statement in your employee handbook. This way, the employee is provided very clear notice that the intent of the policy is to help ensure the security of proprietary company data as well as the privacy of the employee… And that a violation of the policy can lead ultimately to termination.
There are a few other items you may want to look at:
- Verify if the employees’ password has been compromised on the web. This is as easy as visiting https://haveibeenpwned.com, then entering the employee email address. Anywhere the password has been compromised, the employee must then change the password, as well as every other site where that same password is in use.
- I’d be tempted to have your IT person work with your employee to view all stored passwords. This will give you a good idea of what sites are using the same passwords, and then where to change the passwords.

by Marc Mintz | Dec 22, 2022
Well, this is embarrassing. For the first time in nine years, we have a quality control issue at The Practical Paranoid. At some point in the publishing process for Practical Paranoia macOS 13 Security Essentials, we released a version with a few old (macOS 12) assignments and screenshots.
The fully correct and updated Live! and Kindle book will be available by next Tuesday (December 27, 2022), with the print version available within a few weeks (simply can’t rush the printing press).
If you have purchased any Practical Paranoia macOS 13 Security Essentials book version, we are offering a free replacement!
Paperback
- Tear off the cover (verify it specifies a title for macOS 13) and the Proof of Purchase page.
- Complete the Proof of Purchase page.
- Mail both cover and Proof of Purchase page to:
Marc Mintz
The Practical Paranoid
1000 Cordova Pl
#842
Santa Fe, N 87505
- We will ship your free paperback book just as soon as we receive them from the print house.
Kindle
- (Wait until after December 27, 2022) Delete your copy of the book from your Kindle device.
- Go to your Kindle library.
- Select Practical Paranoia macOS 13 Security Essentials.
- The updated book will download to your device.
Live!
- (Wait until after December 27, 2022)
- Open your browser to your Google Drive > Shared with me > Practical Paranoia macOS 13 Textbook folder.
- The new version is waiting for you!
Questions? Please contact our office at info@thepracticalparanoid.com

by Marc Mintz | Sep 19, 2022
Just when you thought it was safe to go back into the water.
Oh, wait. Wrong movie!
Do you have a credit card? Do you have a cell phone? Of course you do! And if a bad actor gains access to both of these, they have found an effortless way to gain full control over your credit card account.
The Hack
This hack was discovered when the bad actor was caught in the act at in the locker room of a gym. The process works like this:
- The bad actor (BA) opens lockers (at least at the gym) to gain physical access to then victims phone a credit card.
- BA uses their phone to attempt log in to your credit card account, tapping the “Forgot my password” or “Reset my password” button.
- An authorization code is sent to the victims cell phone.
- IF (big if) the victim has configured their phone to display messages while in Lock Screen mode, the authorization code is clearly visible to BA.
- BA enters the authorization code on their phone. This gives BA the opportunity to change your password, phone number, email address, and all other vital information.
- At this point, BA has full control over victims credit card account.
The Fix
Fortunately, the fix is straightforward and simple. All that need be done is to prevent messages from displaying on your Lock Screen. If you have followed me for any time, you know I’m a fan of not allowing ANYTHING to display on the Lock Screen.
For those of you who have just upgraded to iOS 16, this can be done from Settings > Notifications > Messages > disable the Lock Screen option. It is OK to leave Notification Center and Banner notification enabled.
For Android users, open Settings > Privacy > Notifications on Lock Screen > enable Don’t show notifications at all.
50% DISCOUNT ON ALL PRACTICAL PARANOIA BOOKS
IOS 16 AND IPAD 16 ARE NOW AVAILABLE
And so are the vulnerabilities to your device, data, and communications!
iOS 16 is the MUST HAVE upgrade for your iPhone and iPad. In addition to dozens of new features, iOS 16 has dramatically improved the options for your cybersecurity and internet privacy.
But you need to know HOW to properly configure your device to ensure your security.
Practical Paranoia Security Essentials has been doing just that for over 8 years at the best-selling, easiest, most comprehensive guid to securing data and communications on your home and office devices.
And from now until September 30, 2022, ALL Practical Paranoia Live! Edition books are 50% off!
Visit https://thepracticalparanoid.com to order at half price today. Just enter discount code “50” at check-out.
All Practical Paranoia Security Essentials books are available in paperback, kindle, and Live! editions.
Live! editions are exact replicas of the paperback and kindle editions, made available through Google Drive. This is the version used by Universities, trade schools, and high schools, and is now available to everyone. Its advantages include: Always available on any device with a browser and internet connection, and automatically and constantly updated as the OS, applications, and best practices evolve.
Questions, call +1.505.453.0479
![]()

by Marc Mintz | Aug 26, 2022
As reported in the August 25, 2022 edition of AppleInsider (https://appleinsider.com/articles/22/08/25/google-tracks-39-types-of-personal-data-apple-tracks-12), of the five major Big Tech firms, Google tracks more personal data than any other, and Apple tracks the least.
Google was found to track 39 data points per user, Twitter tracks 24, Amazon 23, Facebook 14, and Apple 12. According to the report, Apple tracks only data that is required to maintain the user account.
Unfortunately, there is no documentation on what data points are tracked.
WHY DO YOU CARE?
Perhaps you don’t care. But if you do, this information is important so that you can make fit decisions and choices for how you use your computer, software, and internet.
WHAT CAN YOU DO?
Although I’ve written 18 books on what you can do about personal data tracking, I’m also not foolish enough to think everyone will rush out and buy an armful of them (but please do). There are some simple steps anyone can take to stem the hemorrhaging of your data into government and advertiser servers:
- Use a privacy-centered browser. These include: Safari, Brave, and Firefox. All free.
- Use a quality VPN (Virtual Private Network) anytime you are online. My personal choice is NordVPN.
- Use a unique and strong password (15 or more characters) for every website and service.
- Use a quality Password Manager to store your overflowing list of unique and strong passwords. My personal favorite is Bitwarden. $10/year.
- Enable 2-Factor Authentication (also called Multi-Factor Authentication or One Time Use Password) for every site and service that provides for it. Then use Bitwarden to generate your 2-Factor Authentication codes.
- Use end-to-end encrypted text, phone, and video conference. My personal choice is Signal. Free.
- Use a quality anti-malware utility. My personal choice is Bitdefender.
- Only download software from legitimate sources. This is usually restricted to either the developer or the Apple Store, Google Play Store, or Microsoft Store.
- Verify at least weekly that your operating system and applications are current.
- Review your security and privacy settings for each of your social media platforms.
WANT TO BE PROTECTED LIKE THE PROFESSIONALS?
Practical Paranoia Security Essentials books have been the best-selling, easiest, and most comprehensive DIY guides for Android, ChromeOS, iOS, macOS, and Windows for nine years. Written by cybersecurity and internet privacy professionals for new and non-technical users, the reader is taken through an illustrated step by step process to secure their data in the same way the government secures their systems. We’ve made it so easy that anyone can confidently do it!


by Marc Mintz | Aug 24, 2022
I normally don’t post any of the daily cybersecurity alerts that post my desk. If I did, I would quickly fill up my 4TB local storage! But this is significant enough to warrant attention.
Hikvision is a highly popular camera manufacturer that is found around the world, with the USA having the second largest implementation–often as security video cameras. A severe security vulnerability was found last year, but it was reported 20220823 that over 80,000 of these units have not yet had their software updated.
Without the software security patch, these cameras are easily accessible by governments, criminals, and your everyday troublemaker.
To quote from the original source material:
Last year, Hikvision resigned from the Security Industry Association (SIA), the largest trade organization for surveillance vendors, after being accused of working with the Chinese Army on research to improve the ‘lethality’ of missiles.
Due to the one-two punch of the gaping and continuing vulnerability, and that Hikvision has resigned from the SIA, we can not recommend their use. We do recommend that should you have a Hikvision video camera in use, replace it ASAP.
Original source material: https://therecord.media/experts-warn-of-widespread-exploitation-involving-hikvision-cameras/

by Marc Mintz | Jul 17, 2022
Want to be a book reviewer while quickly and easily securing your cybersecurity and privacy?
Complete the 60-second application:
<https://docs.google.com/forms/d/e/1FAIpQLSccuqYe0ak5AELTwr71RR6Vwp7yq6ON2uU_l-yL26naBKar0w/viewform?vc=0&c=0&w=1&flr=0>
The Practical Paranoia Security Essentials book series (Android, Chrome, iOS, macOS, and Windows) have been the best-selling, easiest, and most comprehensive DIY and STEM textbook on cybersecurity and internet privacy for over 8 years. Designed for the novice and non-technical user, while providing all of the substance demanded for IT professionals. Discover how fun and easy it can be to secure your personal and business digital life, all while making the best books even better!
Requirements:
- Read the entire book (in streaming PDF format)
- Make notes on technical, grammar, typo, etc. errors.
- Complete reading and comments within three weeks.
- Post an honest review on Amazon.com (once the book is published.)
What You Get Upon Completion of the requirements:
- Signed paperback copy of the book.
- Licensed Live! copy of the book.
- A few “thumbs-up” in your positive karma column

by Andi West | Jan 11, 2022
In what has to be one of the most out of character moves ever, Microsoft recently released a registry hack to install Win 11 on a system that does not meet the minimum hardware requirements set by Microsoft. Why would they do that? It’s a good question that I do not know the answer to, but if allowed to speculate, I have a hypothesis or 2. To get there, let’s go back the beginning of the Win 11 adventure.
- October 2019– Microsoft announces the development of a dual screen friendly version of Win 10 named Win 10x. MS’s primary stated reason for the new OS was to allow Windows to run on dual screen PCs and laptops with external monitors. For those of us who have been using multiple monitor configurations on Win machines for years, this made very little sense.
- May 2021– Microsoft announces it will no longer be developing Win 10x. The project was put on indefinite hold. Following on the heels of that year’s continued global cancellation of civil liberties and in person human contact, this cancelation went mostly unnoticed.
- June 2021– Microsoft announces that it is nearly ready to release Win 11, which came as a bit of a surprise since this was the first mention of the new OS. Also, MS had claimed 10 was going to be the last OS they would release. It was envisioned as an evolving platform and held true to that for about 6 years.
- June 2021 additional– Microsoft sets the minimum system requirements to an arbitrary standard that would negate the ability to run Win 11 on nearly 90% of the factory built PCs* currently in use, 99% of gaming systems**, and 100% of virtual machines***. Even I had to pick up new equipment to install the dev and beta versions from the Windows Insider Program.
- October 2021– Win 11 is officially released. Almost immediately, followed by about a half a dozen published ways to bypass those requirement during install and/or regular operation. The simplest of which is to replace a single Win11 registry key with the Win 10 version of the same key.
- October 2021 additional– Microsoft publishes the Win 10 key to bypass their own requirements, without mentioning that it is simply the key from Win 10.
Hypothesis #1– Not to sound like a conspiracy theorist (mostly because the process by which MS releases and names its operating systems does not qualify as a conspiracy), I think it is fairly safe to say that Win 11 is Win10x with a new desktop style and very little else in the way of new anything. Microsoft has always built their new OS on top of the previous OS and all the core administrative functions, going back to XP, are readily available in Win 11. This release is, however, quite a few less shiny new bells and whistles than usual. My only guess is that the OS was intended to enforce an equipment upgrade across the globe, but they reasoned that the registry key bypass was too much of a tell of their tactics, so they tried to get ahead of it by publishing it in a way that didn’t involving the public noticing the Win 10 & 11 similarities.
Hypothesis #2– They realized that they had limited their new OS’s adoption to about 10% of existing systems* by excluding anything older than a few years, most gaming systems, and virtual machines. This bypass does not help gaming** or virtual*** machines, but it does expand their potential Win 11 customer base to include factory built machines within the last 3 years.
Whichever hypothesis is correct (it is most likely a combination of #2 plus a few other reasons), this seems like a continuation of corporate America’s unwritten policy of cost cutting by skipping in house funded product testing in favor of a general rollout to the public of a beta level product. The results of which could, theoretically, be the cause the historically frequent cascade of OS release problems and their immediate patching with less than optimal fixes, which we’ve experienced with every major Win OS rollout in the last 20 years. Sounds similar to something else Gates has been rolling out lately, doesn’t it?
- Best Practices****
My advice? Simple. Never be an early adopter of Gates inspired technology. It has rarely been rigorously tested or even proven to be a benefit to anyone until the first few service packs or patches have been released.
*TPM 2.0 has only recently been added to and put into use in production model PCs.
**Gamers rarely add security hardware to their self built systems.
***Virtual machines are just that. Virtual. Therefore they do not have hardware TPM’s installed.
****The best thing about Best Practices is that there are always so many to choose from.

by Marc Mintz | Dec 4, 2021
A: VPN was initially designed to be used by computers. As such, there are software and network drivers to install and configure. The problem with IoT devices (Internet of Things, such as wireless thermostats, webcams, remote doorbells, wireless garage door openers, etc.) is that with almost no exceptions, developers have not included an option to add 3rd-party software and drivers. So by themselves, IoT devices cannot be secured.
BUT…
What if we were to do the following:
- Create an encrypted wi-fi for the IoT device to communicate on between your router and the IoT device.
- Enable VPN on the router, so that IoT data is encrypted between your router and your VPN provider.
Doing so makes it exceptionally difficult for your IoT data stream to be intercepted and harvested. No more threat of bad actors snooping on your home or business webcam, or remotely unlocking your digital door locks.
What Can We Do?
Encrypted Wi-Fi
The first step is to ensure your Wi-Fi router is configured properly for secure, encrypted networking.
The current encryption protocol of choice is called WPA3. Unfortunately, it has only been a standard for a year. There are few routers available to support it, and fewer IoT devices supporting it. However, I strongly recommend upgrading to a modem capable of WPA3 so that it is available as you upgrade your networkable devices.
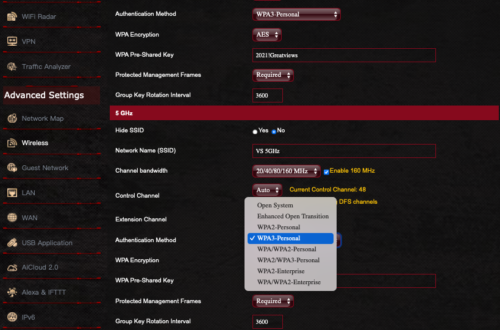
My preference is for the ASUS brand of what are called Wi-Fi 6 or 6e routers. These are much faster than the previous generation, and support WPA3 and WPA2. I will use screenshots from the ASUS GT-AXE11000.
- Open the router control panel.
- From the sidebar select Wireless.
- Scroll down to the Wi-Fi channel you want to use for your IoT devices.
- Tap the Authentication Method. You will see a pop-up menu of all the available encryption options.
- Select WPA3-Personal, then configure the password.
- Save your changes.
- Test your IoT devices, computers, tablets, and mobile phones to determine if they can connect to WPA3.
- If all connect, we have rainbows and unicorns. If some devices cannot connect, you may need to change your Authentication Method to WPA2/WPA3.
- NOTE: Under no circumstances should you need to use WPA. This is a recipe for disaster. WPA has been broken, and any kid with 10 minutes of internet search will find the way to do it. Although WPA2 has also been broken, it is a more complex process.
Configure Your Router for VPN
The next step is to configure your router to connect to the internet via VPN. In this strategy, all traffic leaving the router is encrypted.
NOTE: Many mid-grade routers lack the ability to add VPN. This is a great time to invest in a modern, high-quality router that can add VPN, uses WPA3, and supports Wi-Fi 6.
- Subscribe to a quality VPN provider. I personally use NordVPN.
- From your VPN provider website, download their opvn file. This is the driver to be added to your router.
- Open your routers control panel page.
- From the sidebar, select VPN.
- From the tabs, select Fusion VPN.
- Under the Server List section, tap Add Server.
- In the Add Server window, select OpenVPN tab.
- Enter your VPN subscription username and password.
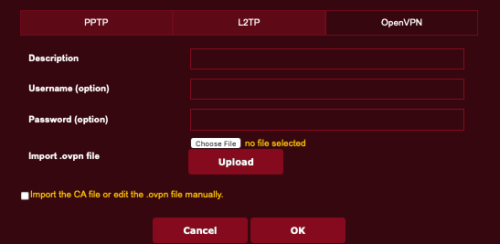
- Tap the Choose File button, then locate and select the opvn file downloaded in step 2.
- Tap the Upload button to upload the opvn file to your router.
- Tap the OK button.
- Returning to the main VPN page, in the Exceptions List area, tap the Add Exceptions.
- In the Create New Policy page, from the Client Name field, tap the drop down arrow to see all devices connected to your router.
- Select one that you wish to be protected by VPN.
- In the Connection Name field, select the name of the VPN policy you created in step 8.
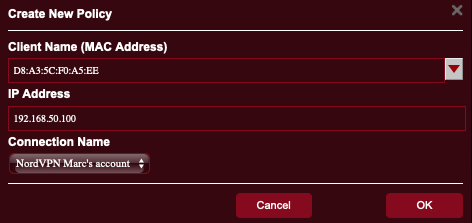
- Tap the OK button.
- Repeat steps 12-16 for every other device to be protected by VPN.
Yes, there are a lot of steps, but they are all easy, and the entire process may take under 10 minutes – AND you get to secure all your devices with VPN.
![]()

by Marc Mintz | Dec 4, 2021
A: Get 100 consultants in a room, end up with 100 opinions.
A bit of background information for those not familiar with Tor. Tor was created by the US Navy as a method to create secure, anonymous internet communications. It was soon after released from restricted government use for use by anyone.
The way Tor works is it is a network – called the “Onion Network” – that consists of three gateways that anyone using Tor must pass through. This includes an entry node, middle node, and exit node. All traffic over Tor is encrypted, and because the exit node knows nothing about user data from the entry node, the data is well anonymized. The user needs to use a browser that understands how to use the Onion Network. The officially recognized browser for use is called the Tor Browser.
From my perspective, I can’t recommend the use of Tor at this point. My reasons are:
- Due to the need to pass through 3 separate nodes, with encryption/decryption occurring at each, there is a huge latency (delay) introduced. This may slow down your internet work by as much as 4-10x.
- The US government (and probably many other governments) have their own nodes in play. If you control a node, you have access to the decrypted data.
- For the past few years a rogue player has installed around 900 nodes – out of a total of 9,000-10,000 total nodes. This one bad actor controls up to 10% of all nodes. Given that when using Tor you have to pass through 3 nodes, chances are around 30-35% your data will pass through one of theirs.
- The entire Tor node system is volunteer, and from all reports, poorly managed and supervised. I can very well see that at least 50% of all nodes are controlled by bad actors.
What to Do
Instead of relying on Tor, I very strongly recommend the 24/7 use of a quality Virtual Private Network service (VPN). With VPN, all of your internet traffic is encrypted as it exits your device, where it travels to the VPN provider, is decrypted, and sent on its way. This prevents harvesting of your data by someone snooping on your Ethernet, Wi-Fi, or cellular connection, your Internet Service Provider (ISP), and anyone else up to the VPN provider. And since your data stream is intermingled with potentially thousands of other users as it leaves the VPN provider, it is impossible to isolate your data.
In addition, when using a quality VPN, your internet traffic is only slightly impacted by the encryption/decryption process – in fact, many users report their internet speed increases when using VPN, as a quality VPN can block some unwanted traffic from hitting you.
There are thousands of VPN providers available. Perhaps the majority are not quality providers and should not be trusted. My go-to vendor of choice is NordVPN at https://nordvpn.com.

by Andi West | Nov 18, 2021
With the roll out of Windows 11, the term TPM 2.0 has been introduced to the general public. What is it exactly? Fundamentally, it is a platform integrity and security device. Beyond that, it depends on who you ask.
For the basics, the TPM (Trusted Platform Module) development has been governed by the TCG (Trusted Computing Group) which is a non-profit (quite lucrative Think Tank) offspring (spawn) of the IT industry (Big Tech). The TCG board is made up of technology manufacturer executives and sadly, has no one from the EFF (Electronic Frontiers Foundation) or any similar consumer advocacy organization, which means caveat emptor as usual. There is a good amount of info to cover about what that means, but for today we will just be discussing what, in a perfect world, the TPM 2.0 was intended to be.
Why was the TPM created?
From Wikipedia– “The primary scope of TPM is to ensure the integrity of a platform. In this context, “integrity” means “behave as intended”, and a “platform” is any computer device regardless of its operating system. This is to ensure that the boot process starts from a trusted combination of hardware and software, and continues until the operating system has fully booted and applications are running.
When TPM is used, the firmware and the operating system are responsible for ensuring integrity.”
Functions-
Encryption– random number generator plus cryptographic capabilities.
Remote attestation*– Device fingerprinting and recognition.
Digital Rights Management– Ensures all media, software, etc. are legitimate and of course, paid for.
What it does not do- Protect your system or data. Although this is being marketed as a consumer protection upgrade, it is merely a corporate profit upgrade. Which is not inherently a bad thing, but they should be honest about it. In the next few posts, we’ll be going over the different hardware and software devices which can be used as TPM 2.0 and in a later installment we’ll go over all the myriad ways one can install, bypass or simply fake this level of compliance. Guess which methods are the cheapest and easiest..
Coming Next Week- Why did Microsoft do an about face on the minimum requirements for Win 11? I have a theory…
*Yes, a topical search of this subject will produce an overwhelming number of papers and articles lauding the privacy and security of the TPM 2.0 and the inherent goodness of remote attestation, but please realize that these were written by corporations, for the benefit of those corporations.
Author’s vaguely connected tangent- And this would be an opportune moment to mention that “By Corporations, for Corporations” is a caveat that must be considered when reading, viewing, or downloading any data nowadays. We are rarely presented with any information that is not in the form of an advertisement. Newspapers are owned by the very entities they used to drag across their pages. Medical studies are announced by press release, not peer review. As Howard Zinn said, “The news is what they hide from us. All we have ever seen was advertising.”
So, always ask this question when experiencing prepared information- Is it BCFC? (Yes, it sounds like a county jail, which is fitting because it has about as much to offer the average human in the way of personal benefit and assistance as a county jail.)
Back to the subject- When one does a less cursory look into the uses of remote attestation, one will find truly dystopian headlines such as-
Sounds legit, right? To sum it up, although there are dozens of RA protocols made by different companies, they all fundamentally function by sending some or all of the exact and most likely, unique, hardware and/or software configuration running on your system and can therefor be used to track you anywhere you go, regardless of VPN, Tor, or any other identity obfuscation techniques you may be using. With this technology, you are literally starting every internet action with an SSL Handshake which proclaims, accurately, exactly what you running. This can easily be tracked as a single entity with database of past actions. If that database is connected to any other entities’ attestation database, (Note that there are only a few mega corporations owning everything nowadays) it quickly becomes the complete digital representation of you. Translates to- knowing exactly who you are and what you are doing at any time online and will be used to predict and manipulate your actions in the future.
What can be done about this? Um… Well, I’m still working on that. Please comment with any ideas you may have. This discussion is definitely open and your input will help.

by Marc Mintz | Nov 17, 2021
A: I can’t speak to your particular issue as I don’t have the specifics, but let me address this more generally.
When you leave your home for vacation and lock the front door, is your home now “secure”? Not if you left the back door unlocked.
When you leave your home for vacation and lock all doors and windows, is your home now “secure”? Not if someone can toss a rock through a window for access.
When you leave your home for vacation, lock all doors and windows, set the alarm, activate the security cameras, notify the police, stop mail delivery, and everything else we have been told to do, is your home now “secure”? Well, a rock through a window, ski masks on the criminals, and smash-and-grab burglary say “no”.
Does this mean it is useless to lock all doors and windows, set up security alarms and security cams? Not at all. Each of us can only do the best that we can to help stave off an attack, making us look like a poor choice as a target.
But back to internet privacy.
All it takes is one small leak for some level of privacy to be lost. A Facebook post showing that you are on vacation will let criminals know your home is not occupied. That MySpace post from 15 years ago where you posted video from a wild party may well be found by the HR department of the company you are trying to get a job. The letter to the editor of your local newspaper where you made negative comments about <some-type-of> people. Yup. You can bet that will come back to haunt you.
So very much of what we do is part of the public record. For under $100 one can purchase a full search of the public record to know most of what there is to know about you. This used to cost thousands of dollars and a private detective.
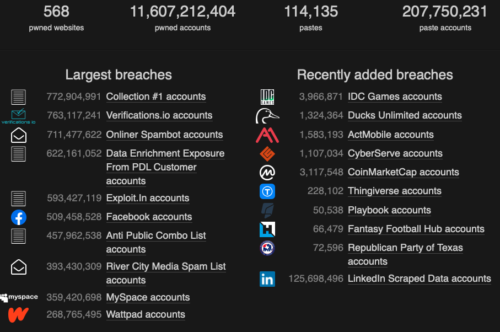
Then we have the daily breaches of major websites. Check out https://haveibeenpwned.com. This provides a listing of the largest and most recent site breaches. In the example below (from November 17, 2021), I can see that IDC Games was recently breached, releasing almost 4 million user records. If you are included in this database, your info with IDC Games is now in someones hands. if they placed it on the dark web, it may be available to anyone with a few dollars to spare.
What To Do
- Get a copy of your credit report from each of the credit reporting agencies in your country. In the US, there are three. If you find any inaccuracy, work with the agencies to remove the information.
- Check the security and privacy settings of all your social media accounts. Most importantly, verify that ONLY your friends have access to your information, and go through your friend list, kicking out anyone who is not a “real” friend. Go through all of your postings. If any posts show you at less than your best self, delete them.
- Keep your computer, tablet, and phone systems up to date. Out of date systems are far more vulnerable.
- Install a quality anti-malware utility. I always recommend Bitdefender.
- Use VPN at all times to encrypt your data coming and going to the Internet. I’m fond of NordVPN.
- Be mindful of phishing attacks. These are usually emails that appear to be from a legitimate source, but are actually not, asking for personal information.
- NEVER post anything on the Internet you wouldn’t want to see on the front page of the news. Because at some point in time, it MAY end up on someone’s front page.
Care to go deeper, with step-by-step DIY guidance just like the cybersecurity professionals use? Visit https://thepracticalparanoid.com.
![]()

by Marc Mintz | Nov 17, 2021
A: Short answer: No.
Phishing is an attempt to gather information from someone while posing as someone or something else. For example, receiving an email that appears to be from your bank, asking for you to confirm your social security number.
As most phishing comes in the form of email or web page, the only way that a firewall could prevent this is to configure the firewall to block all incoming email and access to web sites.
In the case of phishing, the solution is user awareness:
- Install quality anti-malware software. My recommendation is Bitdefender.
- Configure your devices for automatic updates, and verify weekly they are up to date.
- Protect your accounts with multi-factor authentication.
- Maintain daily local and off-site backups.
- If you are asked for information, verify the source of the request
The Federal Trade Commission has more information on phishing at https://www.consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
Remember that phishing is just one very small part of maintaining your cyber hygiene. To help ensure your security and privacy, cover all of your vulnerabilities. The very best DIY book to guide your though can be found in our Practical Paranoia Security Essentials series.


by Marc Mintz | Oct 26, 2021
A: Great question! Few people ever give thought to the browser they are using, and just grab the one in front of them.
Let’s start with the 800 pound gorilla in the room–Chrome.
Google created an open source browser called Chromium. There are dozens of browser available that are based on Chromium, Chrome is one of them. So Google started with open source code, and then added their own proprietary code to make Chrome. Chrome is one of the most full-featured browsers available. The bad news is that it comes configured to feed everything you do on the web to Google as part of its data harvesting. Even if you install all the right extensions to improve the security and privacy of Chrome, there is no way to stop all of its harvesting of your data.
Brave is also based on Chromium. The big difference between Brave and Chrome is that Brave ships with almost all security settings properly configured to help ensure a secure and private internet experience. Brave has been one of my three favorite secure browsers from the day it was released. Because it is based on Chromium, it can use almost every extension that is available to Chrome. Unfortunately, because the underlying framework is Chromium, there may be no way to completely prevent Brave from sending some of your data to Google.
Firefox is not based on Chromium. This is huge. Of all the major browsers in the current market, it is the only major player to do so. This plus being open source helps to make Firefox very secure (no secret data harvesting to Google). Although there are many extensions to expand the functionality of Firefox, it cannot use Chrome extensions.
So, which is the most secure? Out of the box, Brave is far more secure than Firefox. However, if you are willing to install maybe three extensions and manually configure the preference settings, I think the nod may go to Firefox.

by Marc Mintz | Oct 26, 2021
A: Actually, changing passwords on a routine basis is very old school, and is no longer mentioned in any US government cybersecurity guidelines.
What was found is that the more often people are forced to change their passwords, the sloppier they became with password creation – making passwords that were easier and easier to hack.
The current guidelines are to:
- All passwords should be strong. That definition changes by which authority you ask – typically 8 or 16 (and sometimes more).
- Every site and service should have its own unique strong password.
- Passwords should be securely stored. Having passwords written on a post-it note on the bottom of ones keyboard does not meet the criteria. This is where the power of a quality password manager (PM) comes in. A PM will automatically create very strong passwords, store them encrypted form on your device. The better ones will allow you to share your passwords among all of your browsers and devices. My favorite – Bitwarden – also serves as your 2-Factor Authentication software.
- Whenever possible, use 2-Factor Authentication.
- You only need to change your password when it may have been compromised. A good place to check this out is https://haveibeenpwned.com.

by Marc Mintz | Oct 13, 2021
As reported in a study released 20211006 by University of Edinburgh, UK and Trinity College, Dublin, Ireland, despite the public discontent over data harvesting by big tech, it is (of course) worse than any of us thought.
The researchers found that Android devices, with the notable exception of /e/OS devices, even just out of the box with no other installations and sitting idle, these devices harvest great amounts of user info to the OS developer and third parties such as Facebook, LinkedIn, Microsoft, and Google.
Of greater concern is that this data collection offers no opt-out. Many of the apps cannot be uninstalled. Android users are powerless to stop this harvesting. To make matters worse, it was found that for some system apps such as mini.analytics (Xiaomi), Heytap (Realme), and iCloud (Huawei), the encrypted data stream can be decoded, making your data vulnerable to main-in-the-middle attacks.
Think resetting your Google advertising identifier will clear up the situation? Nope. The data-collection system easily re-links your old ID with new ID.
Then you just have to love the response Google provided: “While we appreciate the work of the researchers, we disagree that this behavior is unexpected–this is how modern smartphones work. As explained in our Google Play Services Help Center article (and I know every one of you has read this), this data is essential for core device services such as push notifications and software updates across a diverse ecosystem of devices and software builds.”
Grrrrrrr.
What You Can Do About It
The first option is to grin and bear it. This may be a reasonable position to take. After all, it is little ol’ you against a multi-trillion dollar industry. Might as well let the fricken’ blood suckers take all of my personal data and let me get on with my life.
Or, you can make life a little more difficult for them.
I’m fond of the life lessons story about two hikers out in the woods that come across a hungry grizzly bear. Hiker A asks Hiker B “how fast do you have to run to escape a grizzly.” Hiker B replies “just a little faster than you!”
Going the Android route simply makes it literally effortless for big tech to harvest your data.
Going the Apple route makes it more difficult. Apple has been taking strong steps to block some – not all – of the harvesting of your data. And it looks like with each update they are closing off more avenues to your private life.
Replacing your Android device with an Apple iPhone will go a very long way to helping secure your cybersecurity and internet privacy.
If you are interested in other ways to maintain your freedom, we have the very best, easiest, and most comprehensive DIY books available. Visit https://thepracticalparanoid.com
![]()
by Marc Mintz | Oct 6, 2021
Something few of us pay any attention to is the location data that our mobile device is collecting and sharing. Literally every single step you take is recorded, archived, and sold. Based on your location data, your gender, income, political leanings, education, pregnancy status, and more can be inferred. Once this information has been sold, it can be used not only for marketing, but to spoon feed you targeted news and alerts.
It has been used to discover who attends political meetings and rallies, Planned Parenthood, or Burger King. Most recently, the data location of those who downloaded a Muslim prayer app have been targeted by the US government, and a Catholic news outlet used data location to out a priest who frequented gay bars.
If you think there isn’t a target painted on your back (or the soles of your shoes), then why is location data – including YOUR location – currently a $12 billion yearly industry?
Visit https://themarkup.org/privacy/2021/09/30/theres-a-multibillion-dollar-market-for-your-phones-location-data for a great review.

by Marc Mintz | Oct 6, 2021
Q: When is it a good time to replace my current router with a new unit?
A: NOW! (Really)
What is a Router?
A router is a hardware network device that allows other devices (such as computers, tablets, mobile phones, printers, smart watches, smart doorbells, webcams, etc.) to connect to your local area network (LAN), and then trough the router, communicate with each other (such as sending a file to be printed, or opening a file on the server), and connect to the internet.
As the router is the hub of all of your network activity, a failure or hack at the router means a catastrophic failure of your network and all devices, and a potential hack of all your devices.
Why Replace My Router Now?
Network technologies have changed significantly in just the past few years. If your router is more than 2 years old, it very likely is no longer considered highly secure. This puts ALL of your data from ALL of your devices at risk.
In addition, many of the latest routers include additional security software to help monitor your devices and network for breaches. Earlier routers pretty much let data in and out without any examination.
At the enterprise level (large businesses) Cisco, Jupiter, HP are among the go-to providers of networking equipment. These units have always had security software built-in. They also typically have upgrade options to ensure your always have the latest and greatest features available to you.
This is why these units cost upwards of 5x the cost of prosumer models.
For the purposes of this blog, I’ll not discuss the enterprise, as it is a rarified field demanding one-on-one discussions for your particular environment.
But, for the home user and the small and medium-sized business, prosumer routers can have excellent performance and features, at very affordable prices.
Wi-Fi Encryption
Earlier wi-fi router models used WPA2 for their encryption protocol. Ratified in 2004, this was considered fairly secure. However, it could be hacked. Which is one of the reasons it was replaced in 2018 with WPA3 encryption. Routers with WPA3 capability started shipping in 2019.
Note: If you have older devices (computers, tablets, etc.), they also may be capable of using WPA2, but not WPA3. This makes your older device a security vulnerability. And if you don’t replace the older device, you will need to enable WPA2 on your router for the older device to use the network. This immediately makes the entire network vulnerable.
How to Enable WPA3
For almost all routers, enabling WPA3 is not much more than a tap. For this example, I’m using my favorite prosumer router, the ASUS GT-AXE11000.
- Open a web browser to the control panel of your router.
- Navigate to the Wi-Fi settings.
- Select WPA3-Personal.
- Save.
- The router may restart to initialize the new encryption.
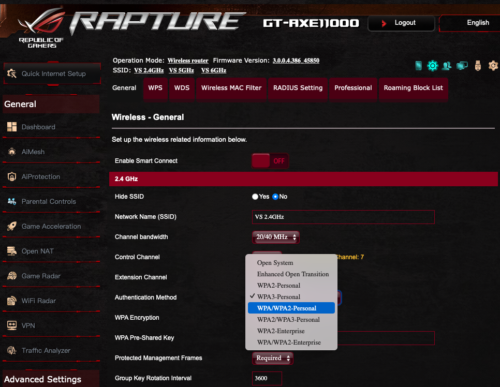
If you don’t see the option for WPA3, it is time to replace your router with a current model.
Network Security
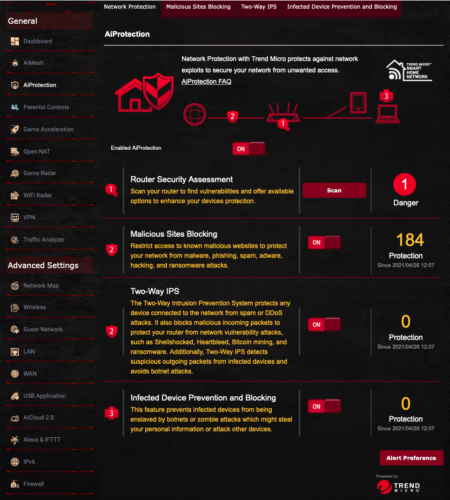
All consumer-grade, and most prosumer-grade routers lack significant network security beyond a rudimentary firewall. One of the reasons I love the ASUS line is the higher-end models include very good network security.
Here you can see how it protects the network by:
- Self-analysis, pointing the administrator to configurations that my not be fully secure.
- Logging the malicious sites users or malware have attempted to access and have been blocked.
- Two-Way IPS blocks attempts malicious packets from reaching your router or network devices.
- Infected Device Prevention and Blocking prevents infected devices from releasing your sensitive information.
Replacing Your Old Router With New
Older routers were pretty much a plug-and-play device, and any user could set it up.
The only downside to the newer security-conscious devices is they do require some reading to do the job right. And even then, I recommend hiring an IT professional to spend the hour or two to properly install and configure. In the case of the ASUS, there are over 100 settings that require attention.
Another Bonus With Your Upgrade–Speed
Although security is the main reason to upgrade your router, there is a bonus available – better performance and speed.
Older routers will typically max out on their wi-fi speed at 300, 600, perhaps 1000 mbs. In addition, they are limited to the 2.4 GHz and 5 GHz channels. The 2.4 GHz channel is overly crowded – sharing bandwidth with microwave ovens, garage door openers, wireless phones, bluetooth devices, and almost any other wireless device. Think of driving in Los Angeles freeway traffic. The posted speed limit may be 65 mph, but with bumper-to-bumper traffic, everyone is going 15 mph.
Newer routers will still have the legacy 2.4 GHz and 5 GHZ to support older devices, but may now include the 6 GHz channel. As this is newly opened, few devices use it, so it is just you and a few other cars on the freeway.






























