
by Marc Mintz | Dec 4, 2018
The Problem
As reported in the December 4, 2018 SpreadPrivacy.com article, when performing internet searches using Google, the results were personalized for the user even when logged out of the user’s Google account, and when in Incognito Mode.
The bottom line is that Google is using identifiers other than Google account login to identify users when searching. This can be easily done using the digital fingerprint of the device.
To be fair, Google will tell you that personalizing search results is a feature of using Google search. That based on each users search and browsing history, Google will filter and prioritize search results to best meet the world view and preferences of the user. For example, if you browse politically conservative websites, when performing searches of a political nature, you are likely to see links to articles more favorable to the conservative perspective than would someone who browses liberal websites.
Up until now, it was assumed such search filters were in effect only when logged in to ones Google account. But that is now known to be incorrect.
The Solution
If, as Google believes to be true, you prefer having your internet searches filtered so they better align with your world view, then you need do nothing!
However, if you would prefer to have a more accurate view of the world through internet searches, there are a few steps to take:
- Stop using Chrome as your web browser. Replace it with Firefox, Brave, or Safari. These three browsers do not monitor or record your browsing history.
- Replace your default search engine with DuckDuckGo (DDG). DDG doesn’t monitor or record your search or browser history. It submits your search request to dozens of search engines, takes the results, eliminates duplicates, and presents an accurate search result.
- Firefox: Visit https://duckduckgo.com, and then follow the on-screen instructions.
- Safari: In Safari Preferences, set the default search engine to DuckDuckGo.
- Brave: In Brave Settings, set the default search engine to DuckDuckGo.
- Replace your default DNS provider. DNS is what translates https://websitexyz.com to an IP address your computer knows how to find. Most DNS services monitor and record your internet traffic, and make it available for sale. Use a DNS provider that does not do this. There two most popular are Cloudflare (1.1.1.1, 1.0.0.1) and OpenDNS.
- Cloudflare: Cloudflare may be the world’s fastest DNS service. Until recently it had been our go-to solution. I still consider it excellent. However (gotta hate those “howevers” in live), it appears to be going through some growing pains at the moment, resulting in occasional failed service). Go to your Network Settings, delete the current entry for DNS, and replace with 1.1.1.1 and 1.0.0.1.
- OpenDNS: OpenDNS is the great granddaddy of anonymized DNS services. In addition to their free service, their for-fee services allow filtering of content. Go to https://www.opendns.com, sign up for a free account, and then go to your Network Settings, delete the current entry for DNS, and replace with 208.67.222.222 and 208.67.220.220.
- Block Web Trackers. Most commercial websites use web trackers. These monitor all of your activity on the site. This information may be used exclusively by the website, but is more likely to be sold to advertisers (including Google). It is best to block web trackers. My preferences is to use the Ghostery browser extension.
- Brave, Firefox, and Safari: Open your browser to https://www.ghostery.com. Follow the on-screen instructions to download and install the Ghostery extension. Once installed, select the Ghostery icon to configure settings.
- Obfuscate Digital Fingerprint. By continuously changing your digital fingerprint, or by forcing your digital fingerprint to look generic, it becomes difficult or impossible for websites and web trackers to know who you are or to follow your browsing history.
- Safari: Safari (macOS 10.14) automatically generates a generic digital fingerprint. Nothing you need to do.
- Brave and Firefox: You’ve already solved the problem by completing step 4 above. Ghostery also continously modifies your digital fingerprint.
Next steps
These are just the tip of the iceberg for online privacy. Want to fully secure your computer, data, and identity? The Practical Paranoia Security Essentials books have been the #1 best-selling and easiest to follow DIY cybersecurity series for over 5 years! Available now at 50% discount for our online Live! edition.


by Marc Mintz | Nov 27, 2018
A: The NIST SP 800-171 is a best-practices form, something like a checklist on steroids. It is created and produced by NIST (National Institute of Standards and Technology), one of the two federal teams charged with helping to ensure cybersecurity. The other is US-CERT (United States Computer Emergency Readiness Team).
NIST is governed by the U.S. Department of Commerce. US-CERT is governed by the U.S. Department of Homeland Security.
There is a core problem with cybersecurity–how do you know you are doing the proper things, in the proper way, to the proper degree to help ensure (note this is not guarantee) you, your family, and your organization cybersecurity and privacy?
NIST has developed best-practices that help to standardize these questions, and have organized them as best practices into the SP 800-171 form. This form only asks the questions, but does not provide the answers. This may lead you to some head-scratching, but it makes sense because every IT environment is different. It now becomes your job (or the job of your IT or Security Department) to figure out how to answer and resolve those questions.
This best-practice document has become a standard for both cybersecurity and privacy. It is used as the basis of certifying HIPAA-covered entities (health care organizations), SEC-covered entities (finance organizations), Federal and military contractors, and many more. If your organization isn’t using this document, it is almost certain your cybersecurity and privacy are lacking, and may be held legally and financially liable in the event of client data leakage.
By following and answering the 800-171, your IT group has done due diligence to protect your IT infrastructure.
Which, since the document doesn’t provide any guidance to solutions/answers, is where MintzIT comes to the rescue! We have been providing full-service IT consulting to all of New Mexico for 32 years, and are authors of 13 best-selling cybersecurity books, making MintzIT the perfect solution to ensuring your cybersecurity and privacy.
Attached you will find a copy of the NIST SP 800-171. Listed below are a couple example resolutions to the questions.
| 3.1 ACCESS CONTROL |
|
| 3.1.1 Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems) |
- All data stored on Google G-Suite, with access restricted to authorized users using strong passwords and 2-Factor Authentication.
- Accessing company data permitted only on company computers that have passed monthly security audit.
- Access to local computers and data restricted to authorized users using strong passwords and 2-Factor Authentication.
- Local computers are hardware encrypted (Filevault2 on macOS, Bitlocker on Windows 10 Pro).
- Local computer security protected with ASAP OS and application updates.
- Local Area Networks secured with Stateful Packet Inspection firewall at both the router and local computer.
- Local Area Network security protected with ASAP firmware updates for modem, router, switches, and wireless access points.
- Mobile Device access to data on Google G-Suite restricted to authorized users via minimum 6-digit PIN.
- Mobile Device access protected with erase after 10 failed PIN attempts.
- Mobile Devices with access to data are protected with hardware encryption.
- Mobile Device security protected with ASAP OS and app updates.
- Mobile Device security is locked down with Mobile Device Management, preventing end-user from performing any system or application modifications.
|
| 3.3 AUDIT AND ACCOUNTABILITY |
|
| 3.3.1 Create, protect, and retain information system audit records to the extent needed to enable the monitoring, analysis, investigation, and reporting of unlawful, unauthorized, or inappropriate information system activity. |
- Google G-Suite for Enterprise is used for all data, it provides audit records.
- Google G-Suite for Enterprise is used for all data, it provides for data loss prevention.
- Spinbackup is used, it provides for 3rd-party data loss prevention, giving a snapshot-based backup for all G-Suite-based data (email, calendar, contacts, data).
|

by Marc Mintz | Nov 19, 2018
For most of us, almost all of our time on the computer is spent on a web browser. This time is so very valuable to advertisers, that Google paid Apple $9,000,000,000 (yes, 9 Billion dollars) a year just so that Google is the default search engine for Apple Safari.
Why is your web activity so incredibly valuable? Because by watching in literally microscopic detail what you search for, what you spend time looking at, and how you look at it creates a detailed profile of who you are. Google – as well as the other search engines – is able to predict your likes, dislikes, sexual preferences, and behaviors with far greater accuracy than anyone in your inner circle.
All of which allows advertisers to perform targeted marketing with laser precision.
Which by itself isn’t necessarily a bad thing. What may be a bad thing is that this data is for sale to those other than in advertising. The most glaring example is what was done with your Facebook data in 2015-2016 once it made it into the hands of Cambridge Analytica.
If you aren’t already thinking What can I do about it?, may I recommend skipping the rest of this article and go back to watching cat videos.
There are many strategies to anonymizing or cloaking your web activities. How much and what to do depends on what your idea of balance between security and PITA looks like.
EXTREME SECURITY
- TOR. For those requiring the very highest level of anonymizing and cloaking, changing your web browser to TOR is step 1. With TOR in use, your web traffic is bounced from TOR node to node a few times, stripping away identifiable information, before connecting with the target web site or service. The trade-off is a non-trivial performance hit. Because of this, TOR is not for everyone.
- VPN. Virtual Private Network is a web service that provides fully-encrypted communications between your computer/mobile device and the VPN server. From here the data is unencrypted and continued to the target web site or service. This blocks anyone from snooping on your local network and internet service provider from discovering what you are doing. It does, however, give your VPN provider the ability to see all. This is why it is vital to select a quality VPN provider. I’m fond of NordVPN and PerfectPrivacy.
HIGH SECURITY
- DNS. Domain Name System is the internet service that translates English names for a site to the actual server address. But DNS most likely tracks and records every site your device visits. To prevent this, use a DNS service that respects your privacy. I’m fond of CloudFlare. to do this, simply change whatever your current DNS settings are to use the CloudFlare servers – 1.1.1.1 and 1.0.0.1.
- Search Engine. By default, 90% of us use Google as the search engine. And in case you have been sleeping in class, Google has become one of the world’s most profitable corporations by selling your search information. No worries! Just change your search engine to DuckDuckGo. Not only does DDG not track or record your searches, but it is also the best search engine available. This is because when using DDG, it submits your search criteria – anonymously – to all of the major search engines, and then compiles the results for you. To make DDG your search engine, open your browser to https://duckduckgo.com.
- Browser. DDG takes care of your searches, but if you are using Google Chrome or Microsoft Edge, they are reporting on your travels as well. Best to use a browser that doesn’t tattle on you. Brave is excellent, as are Firefox and Safari.
- Trackers and Fingerprinting. Most commercial sites now use trackers. Trackers watch your every move on a site, and then continue to follow you to each subsequent site. You can stop trackers by installing an anti-tracker browser plug-in such as Ghostery. Just visit https://ghostery.com and then follow the on-screen instructions. In addition to blocking trackers, Ghostery also hides your digital fingerprint. This prevents websites from pinpointing your device as it travels the internet.
- Malicious Sites. As more computers have anti-virus software installed, criminal hackers are turning to compromising websites, which will inturn send the data they harvest from you to the criminal. To help block such sites, install a browser plug-in from the anti-virus developer Bitdefender called TrafficLight. Once installed, when visiting a known malicious site, TrafficLight will block the site from loading, and present a warning message to you. You then have the option to continue to the site, or back away.
- Up-To-Date Browser. Browsers play the cat-and-mouse game with criminal hackers, trackers, and advertisers by continually updating their software. Although most browsers are designed to auto-update, that process fails more often than developers admit. If using Chrome or Firefox, you can force an update by opening the browser’s About… menu. Brave is updated from its Check for Updates… menu. Edge and Safari are updated as part of routine OS updates.
- https. When connecting with a website using http://xyz.com, all communication between your device and the site is sent in clear text. Any snoop between your computer and the site is able to see everything. When connecting with a website using https://xyz.com, all communication is encrypted. Snoops can see the site connected with, but cannot see the data. Not all sites have upgraded to use https. For those who have, installing the HTTPSEverywere plug-in will force the https, even if you have entered http.

by Marc Mintz | Nov 5, 2018
A: Although I can’t speak specifically as to why your IT support doesn’t want you to run updates, I can give reasons why MintzIT restricts clients from doing so. Spoiler alert… It’s not because we are power-mad admins trying to keep the end-user under our boot!
Having an authorized, qualified IT technician or consultant be the only one who runs updates, installs applications, and performs maintenance on your computer and other IT equipment is so important, it is actually a requirement of the NIST 800-171 (the gold-standard checklist for cybersecurity practices), and HIPAA and SEC covered entities. In point of fact, all of these best-practices prohibit the end-user from even knowing an administrative password!
- Best practices include everyone – even admins – to log in with a non-admin account.
- The primary reason is that both malware and hackers take on the power of the currently logged in user. If the user is logged in with an administrator account, the malware or hacker can assume full control over the computer. If the user is logged in with a non-admin account, the malware or hacker is usually limited to controlling the user data.
- Another issue with knowing the admin password is that it is almost impossible to know when malware or a hacker are attempting to take over a computer. The best and most common example is when visiting a website and an alert pops up stating your Adobe Flash is out of date – click here to download. It is almost guaranteed this is malware and not the real Flash. But how does an end-user know?
- Most cybersecurity experts go further with mandating all non-admin users log in with Parental Control (macOS) or Child (Windows) accounts. The reasoning behind this is that even the very best antivirus software can only catch 99.9% of known malware. It is estimated there are up to 40,000,000 malware variants in the wild, leaving up to 40,000 known malware that won’t be caught. This number doesn’t include unknown malware, which is almost certain to get through to your system. Some malware has been in the wild for up to 9 years before being found! With a Parental Control or Child account, it is possible to implement Application Whitelisting. This specifies which applications are permitted to launch, anything not on the list cannot launch. Malware, known or unknown would not be on the list, and therefore presents no security issue – unless the user has access to the administrator password to bypass the Whitelist.
- Most security settings on a computer cannot be modified by any other than an administrator account. Every day I see users who know the administrator password bypassing or removing these settings–usually because they see no reason for having them. What they don’t know is that with a click of a button and entering an administrator password, they have taken their computer from fully hardened to fully vulnerable.
- Even in the case of installing updates, there are issues of stability, compatibility, and security that must be researched prior to performing the update. When a user blindly updates something, they run very real risks. It is assumed that their IT professional will be aware of current risk parameters and know how to work around or with them.
So the bottom line is that your IT support is probably trying to keep your computer running smoothly and securely (if you are talking about your own personal computer), or is trying to follow Federal cybersecurity guidelines or legal requirements (if you are talking about a company computer).
If you simply can’t resist clicking that Install Now button, it wouldn’t hurt to call your IT professional first.

by Marc Mintz | Oct 30, 2018
Apple released documentation today on their T2 chip, included with the new Macs released today, as well as the MacBook Pros released earlier this year. The T2 security chip helps to protect encryption keys, encrypted storage, fingerprint data, and secure boot features.
But a vital feature that was unknown until today is that it also provides hardware-level protection of the device’s microphone. When the lid is closed on the new laptops, the internal microphone is disconnected at the hardware level. This means it is impossible for a hacker to eavesdrop on your audio as long as the lid is closed. To the best of my knowledge, no other computer offers this level of audio security.
Of note is that the T2 does not cut off the internal webcam when the lid is closed, because, well, the lid is closed!

by Marc Mintz | Oct 29, 2018
A: Nothing. Fundamentally all you have is an email address.
If you were interested in committing a felony, you could attempt to hack into their Google account. But assuming the user has a strong password and has enabled Two-Factor Authentication, it would be a futile attempt at state-funded housing.

by Marc Mintz | Oct 29, 2018
A: Some malware do nothing until a triggering effect (specific time, amount of time since install, application launched, website visited, etc.)
Some take some action immediately.
Well-designed malware will never present evidence of their presence to the user. This is to say, if you see suspicious activity on your computer, if it is due to malware, it was poorly written code.
The first line of defense is to install a quality antimalware utility. I currently only recommend Bitdefender.
The next step is to have your computer professionally audited to ensure there is no system damage, and that all security measures are in place.

by Marc Mintz | Oct 29, 2018
A: There are a number of standard steps to take regardless of your email provider:
- Use a strong password. The current recommendation is a minimum of 15 characters, in a password that is unique and not used with any other of your websites or services.
- Add 2-Factor Authentication. This significantly adds to the difficulty of accessing your account even if your password is compromised.
- Never allow anyone else to use your computer without first creating a user account for them.
- Install and use a quality antivirus software.
Lastly, as you asked specifically about Yahoo, give some consideration as to why one would continue to do business with a company that was directly responsible for not one, but TWO of the worst cybersecurity breaches in history.

by Marc Mintz | Oct 29, 2018
The US Department of Homeland Security has released an update to their ST15-003: Before You Connect a New Computer to the Internet documentation. With the holiday season approaching (along with all of the new IT systems to unwrap), it’s a good time to review some cybersecurity best practices to help avoid hacking of your credit cards, bank account, personal information, and help support smooth operations. I have outlined the document below:
- Secure your router. A popular method of harvesting all data on your network is for a criminal hacker to infect your router. This security process should include:
- Power-cycle to remove any RAM-resident malware
- Update router firmware.
- Eliminate any unwanted DMZ settings.
- Eliminate any unwanted port forwarding.
- Enable and configure your firewall. Older-style firewalls rely on configuring ports and what type of traffic is allowed. This is quite complex and time-consuming. If you have this type of firewall built into your router, time to upgrade to a new router with Stateful Packet Inspection. These require little more than turning on.
- Install and use antivirus software. I currently recommend using Bitdefender antivirus for every macOS and Windows computer.
- Remove unnecessary software. Every piece of software has some vulnerability. If you don’t use it, remove it.
- Operate under the principle of least privilege. Most malware and criminal hackers take on the power of the currently logged-in user. If your user account is an administrator, they have full control over your computer. Always log in with a non-administrator account. Better yet, log in with a Parental Control (macOS) or Child (Windows) user account to further restrict the damage a criminal can do. I’m hard-pressed to come up with a reason that a computer user ever needs to log in as an administrator.
- Secure your web browser. By default, most browsers have insecure settings. Before surfing the web, verify that all settings and preferences are configured for security.
- NOTE: Better yet, check out the Brave browser. It is built for security.
- Apply software updates and enable automatic updates. The #1 reason for updates are as security patches. It is vital to ensure the timely installation of system and application updates.
- Use caution with email attachments and untrusted links. Criminal hackers commonly use email to infect computers and to harvest information. If you don’t know who sent you an email, don’t open any of its attachments. Before clicking on a link, hover the cursor over it to view the full URL.
- Use strong passwords. The Department of Homeland Security is in charge of all things cybersecurity within the US. Their current guidelines for strong passwords is “Use the strongest, longest password or passphrase permitted”. The NIST 800-171 is a Federal cybersecurity best practices document which most organizations should follow. The current minimum recommended password length is 15 or more characters. I suspect this number will soon be increased to 24 or more. Use a password manager such as LastPass to create, remember, and automatically enter passwords. Your memory is best used for other things.
Whew! That is what needs to be done before connecting to the Internet. For everything that needs to be done after connecting, we have some great books.


by Marc Mintz | Oct 25, 2018
Election Day, November 6, 2018, is just around the corner. Take part in the most important election of your lifetime.
- Not sure if you are registered to vote? Visit https://vote.org.
- Not registered? Register to Vote at https://vote.org.
- Just get it done! Vote early by visiting https://vote.org.
- Out of town November 6? Get an absentee ballot at https://vote.org.
- Find your polling place at https://vote.org.
- Can’t drive to your polling place? Both Uber and Lyft are offering free rides to and from your polling place.


by Marc Mintz | Oct 25, 2018
A new report from The Department of Computer Science, University of Oxford, released 20101018, finds that data harvesting by Android apps is epidemic.
Almost 1,000,000 Android apps from the US and UK Google Play stores were analyzed. It was found that 88.4% shared your data with Alphabet (parent of Google), 42.5% shared with Facebook, 33.8% shared with Twitter, 26.27% shared with Verizon, 22.75 shared with Microsoft, and 17.91 shared with Amazon.
Personally, I’m going to be pulling this stat out at the next cybersecurity cocktail social hour when some Android fan-boy insults the iPhone for being too expensive. Because, precisely what value do you place on your personal data and identity?

by Marc Mintz | Oct 23, 2018
Apple has just released macOS 10.14 Mojave–the most advanced computer operating system ever. It is recommended that all Macintosh users upgrade to take advantage of all the new features, including:
- Stacks automatically organize files on your Desktop
- Finder is more powerful than ever–locate a file by how it looks, instantly see all file metadata, and perform Quick Actions on files without opening the app
- Photos–shoot an image with your iPhone and have it automatically appear on your Mac in Finder, Mail, Messages, Notes, Pages, Keynote, and Numbers
- Facetime allows for group audio and video calls with up to 32 people
- Security–apps are required for your explicit approval before accessing the camera, microphone, and data in Messages and Mail
- Security–a more secure Safari, which prevents website Share buttons and comment widgets from tracking you, as well as blocking advertisers from targeting you based on device fingerprint (this is HUGE)
- Security–automaticly generate and store strong passwords
Right alongside the release of macOS 10.14 is a brand new Practical Paranoia macOS 14 Security Essentials. The best-selling, easiest, step-by-step, most comprehensive guide to securing your home or business macOS computers.
Official workbook for the Practical Paranoia: Security Essentials Workshop, STEM and college cybersecurity courses. Designed for instructor-led and self-study. The entire course is contained within the book. Includes all instructor presentations, hands-on assignments, links to all software, and security checklist.
You don’t need to be paranoid to know they are out there to get your computer, data, and identity.
- 2,000,000 laptops were stolen or lost in the US last year.
- Only 3% of stolen computers are ever recovered.
- Malware attacks on macOS have become commonplace.
- Hundreds of eyes may be able to see your name and password, along with the contents of every email you send.
- Once the bad guy has his hands on your Mac, it takes under one minute to bypass your password to gain access to all your data.
- With a slight bit of social engineering, your iCloud, Facebook, LinkedIn, Google, and other social media accounts, along with all your data, is freely accessible.
- Through PRISM and other avenues, our government has access to your online browsing and email history.
You don’t need to be an Apple Genius to protect your system!
In this easy, step-by-step guide, CIO, Security Specialist, and Certified Apple Consultant Marc L. Mintz takes any macOS user–from the novice with no technical skills, to experienced IT professional–through the process of fully encrypting and hardening the security of their computer, data, email, documents, network, instant messaging, storage devices, iCloud, browsing, and entire Internet experience.
It’s your information. Protect it.
Guaranteed to be the easiest to follow and most comprehensive macOS cybersecurity book available.
Practical Paranoia macOS 10.14 Security Essentials Live!
is available this week at a 50% discount!
Visit https://thepracticalparanoid.com to place your order now.
Sample Views


by Marc Mintz | Oct 23, 2018
Apple released iOS 12 this month–the most advanced mobile operating system ever. It is recommended that all iPhone and iPad users upgrade to take advantage of all the new features, including:
- 50-200% performance improvement
- FaceTime now supports video and audio with up to 32 people at once
- Personal Animoji
- The most advanced Augmented Reality
- Do Not Disturb can now be set for just a meeting or location-based
- A more secure Safari, which prevents website Share buttons and comment widgets from tracking you, as well as blocking advertisers from targeting you based on device fingerprint (this is HUGE)
Right alongside the release of iOS 12 is a brand new Practical Paranoia iOS 12 Security Essentials. Completely revised for the new iOS, this book contains everything you need to fully secure your device, data, web browsing, and communications on your iPhone and iPad. Written for the non-technical user, it uses illustrated step-by-step guides to meet the highest security standards.
It’s your information. Protect it.


by Marc Mintz | Oct 21, 2018
THE HIDDEN DANGER
You know that thumb drive sitting by your computer? That one a friend handed to you, or a client shipped to you, or maybe you found it in the parking lot. Yes, that one. The one you probably already connected to your computer–without realizing the danger.
Perhaps the better way to look at this is, would you put it in your mouth?! You and I don’t know where that memory card has been, nor what malware may have been intentionally or unknowingly acquired.
If the card was given by a friend or business associate, it is quite possible that their computer is compromised with malware. And if that card had been attached to their computer, the card has likely been infected.
Also, a common method of criminally hacking a computer is to place compromised memory cards in a business parking lot, or near a desk. It’s been found that the majority of people will pick up the card, and then insert it into their computer to find what is on it. Of course, all it takes is a millisecond for the compromised card to transfer its malicious payload onto your computer.
WHAT TO DO?
- if you are in a company, NO external storage device should ever be connected to the network or computer without first passing a security audit by the IT department. This is so critically important, it is a Federal cybersecurity guideline.
- This also applies to any external storage device that has passed a security audit, but has since connected to another network or computer.
- If you are a home user you probably have no IT department to perform a security audit. Instead, have your computer technician or consultant perform the security audit. If you have no computer support person, at the very least ensure you have a quality antivirus utility installed on your computer, and that it is fully up-to-date, prior to connecting the memory card. Then run a malware scan on the device prior to accessing the device.

by Marc Mintz | Oct 9, 2018
On or around October 16, 2018, the new Chrome 70 will arrive. if you currently have Chrome installed, it will automatically update.
Core to the new Chrome is an upgrade to security. Specifically, Chrome will no longer trust HTTPS certificates issues by Symantec prior to June 2016. This includes Thawte, VeriSign, Equifax, GeoTrust and RapidSSL certificates. Security researcher Scott Helme found 1,139 sites in the top one million sites ranked by Alexa, including Citrus, SSRN, the Federal Bank of India, Pantone, the Tel-Aviv city government, Squatty Potty and Penn State Federal to name just a few.
HTTPS certificates encrypt the data between your computer and the website or app you’re using, making it near-impossible for anyone — even on your public Wi-Fi hotspot — to intercept your data. Not only that, HTTPS certificates prove the integrity of the site you’re visiting by ensuring the pages haven’t been modified in some way by an attacker. Most websites obtain their HTTPS certificates from a certificate authority, which abide by certain rules and procedures that over time become trusted by web browsers. If you screw that up and lose their trust, the browsers can pull the plug on all of the certificates from that authority. For these reasons, Google stopped supporting Symantec certificates last year after it was found to be issuing misleading and wrong certificates, as well as allowing non-trusted organizations to issue certificates without the proper oversight.
WILL THIS BE AN ISSUE FOR YOU?
Before the new Chrome arrives, check out the sites of importance to you. For example, if you use www.pantone.com:
- Visit this site in Chrome.
- Click the Lock icon in the address bar.
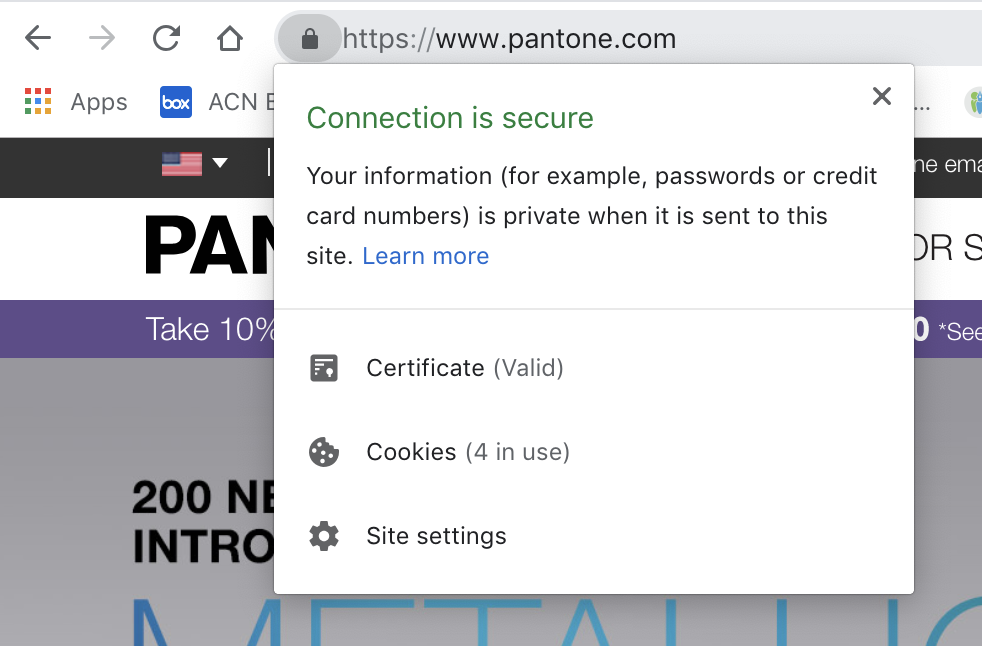
- From the drop-down menu, select Certificate.
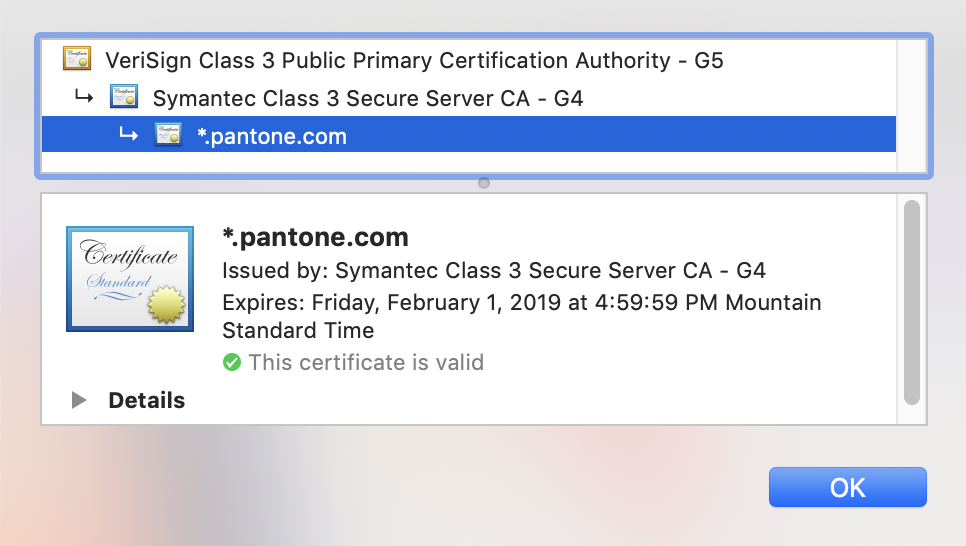
- In the bottom text field, look for the Issued by: text. If issued by Thawte, VeriSign, Equifax, GeoTrust, RapidSSL, or Symantec prior to June 2016, you will have problems accessing the site using Chrome 70.
WHAT TO DO
If an important site hasn’t updated it’s HTTPS certificate after Chrome 70 installs, you should still be able to access the site using other browsers (unless they take the same security stance as Google–none have so stated). Quality alternative browsers include Brave, Edge, Firefox, and Safari.

by Marc Mintz | Oct 7, 2018
Apple has just released iOS 12 for iPhone and iPad–the most advanced mobile operating system ever. It is recommended that all iPhone and iPad users upgrade to take advantage of all the new features, including:
- Speed–Up to 200% faster
- FaceTime–Video and audio sharing with up to 32 people at once
- Notifications–Instant Tuning reduces interruptions
- Photos–Faster, easier, intelligent sharing
- Siri–Create custom shortcuts
- Security–a more secure Safari, which prevents website Share buttons and comment widgets from tracking you, as well as blocking advertisers from targeting you based on device fingerprint (this is HUGE)
- Security–automaticly generate and store strong passwords
Right alongside the release of iOS 12 is a brand new Practical Paranoia iOS 12 Security Essentials. The best-selling, easiest, step-by-step, most comprehensive guide to securing your home or business iPhones and iPads.
Official workbook for the Practical Paranoia: Security Essentials Workshop, STEM and college cybersecurity courses. Designed for instructor-led and self-study. The entire course is contained within the book. Includes all instructor presentations, hands-on assignments, links to all software, and security checklist.
You don’t need to be paranoid to know they are out there to get your computer, data, and identity.
- 3,000,000 phones were stolen or lost in the US last year.
- Malicious attacks have started on iOS.
- Hundreds of eyes may be able to see your name and password, along with the contents of every email you send.
- Once the bad guy has his hands on your iPhone or iPad, it takes under one minute to bypass your password to gain access to all your data.
- With a slight bit of social engineering, your iCloud, Facebook, LinkedIn, Google, and other social media accounts, along with all your data, is freely accessible.
- Through PRISM and other avenues, our government has access to your online browsing and email history.
You don’t need to be an Apple Genius to protect your system!
In this easy, step-by-step guide, CIO, Security Specialist, and Certified Apple Consultant Marc L. Mintz takes any iOS user–from the novice with no technical skills, to experienced IT professional–through the process of fully encrypting and hardening the security of their device, data, email, documents, network, instant messaging, iCloud, browsing, and entire Internet experience.
It’s your information. Protect it.
Guaranteed to be the easiest to follow and most comprehensive macOS cybersecurity book available.


by Marc Mintz | Sep 24, 2018
A: The operating system (I’m assuming this is what you are updating) is only one small piece of the cybersecurity puzzle. Yes, OS updates are primarily about patching vulnerabilities within the OS, but focusing only on this is like locking only your front door when leaving for vacation, while leaving the back door, side door, all windows unlocked, the alarm system off, and taking the dog with you!
Just a few of the other issues to be concerned with:
- Encrypted storage device
- Log in as a non-administrative user
- Enable application whitelisting
- Install a quality antivirus utility
- Install a quality anti-malicious website plug-in for each browser
- Use WPA2 with AES encryption for your Wi-Fi
- Enable VPN for all internet traffic
- Do not allow any unauthorized devices or persons on your network
- Update firmware on all network devices
- Only exchange email with others using full end-to-end TLS-encryption
- Communicate over voice, video, and instant messaging using only end-to-end AES encrypted apps
- Only install apps downloaded from the Apple App Store or from verified sources.

by Marc Mintz | Sep 24, 2018
A: We first need to define your parameters for “encrypted”, and from what/who are you attempting to protect your communications.
VULNERABILITIES
Common points where email is vulnerable to penetration, hijacking, or otherwise accessed by unauthorized personnel:
- Unencrypted storage device. Your email may be end-to-end encrypted, but if either the sender or recipient have a computer or mobile device with an unencrypted storage device, it is child’s’ play to access the data. In the case of macOS, the boot drive should have FileVault 2 full disk encryption enabled. In the case of Windows, BitLocker full disk encryption. iOS devices have built-in hardware encryption. Android, well, good luck with that. Newer Android phones allow you to manually enable encryption. Most older phones do not.
- Weak email passwords. If the sender or recipient email accounts have weak passwords, it is easy to access the email.
- Weak computer passwords. If the sender or recipient computers have weak passwords, it is easy to access the computer, and then instantly access email.
- Weak mobile device passwords. Many people don’t even put a password on their mobile device. Turn your back, the device is taken, and all data is accessible.
- 2-Factor Authentication (2FA). 2FA is the only way we have to secure your email account. Should someone gain access to your email password, with 2FA active, they still will be unable to access your email.
TLS
At the most basic of encryption levels is the communication between the sender and their email server, and the recipient and their email server. The current standard is TLS. If either the sender or recipient do not have a TLS connection to their email servers, the email may be sent in clear text on at least one leg of the journey. You can verify if TLS is active for both sender and recipient at https://checktls.com.
Paubox.com is an inexpensive commercial service that can enforce TLS encryption between computers.
If you are only relying on TLS, beware the email is readable at the sender and recipient email servers. Granted, normally only the email host staff and government personnel have access to this data, but this may include hundreds of unwanted eyes.
ENCRYPTION AT REST
TLS takes care of the encryption in transit, but full security means that your communications are also encrypted at rest – while on the email server. This prevents the email host from accessing your communications, as well as criminals and government personnel. you will need to talk with your email provider and that of the other party to determine if the email is stored encrypted at rest.
END-TO-END ENCRYPTION
The ultimate email standard is end-to-end encryption. This means that the email is encrypted at the sender’s device, all the way through to the recipient’s device. In this way, even the email hosts have no access to the communications. There are several ways to accomplish this:
- PGP/GPG encryption
- S/MIME encryption
- Use a secure server
- Use encrypted attachments
PGP/GPG is free, but is technically challenging to implement.
S/MIME is less technically challenging but requires both sender and recipient pay for S/MIME certificates ( $10-$200/year/account).
Using a secure server is inexpensive ($0-$100/year/account), and very easy to implement. Not much more than signing up for an account. I recommend ProtonMail.com for their long-standing commitment to security and privacy, and offering both free and for-fee services.
Another alternative is to just use the same email service you currently use, but when needing security and privacy, craft your communication as a document, securely encrypt the document, attach the encrypted document to an email, and then send. This has the advantages of keeping the email service you are comfortable with, using applications you are comfortable using, and using strong encryption. The options include (but are not limited to):
- Microsoft Office products. As long as you are using current versions, Word, Excel, and Powerpoint allow you to encrypt their files using AES 256 bit encryption – an industry standard and best practice.
- If using an application that does not include built-in encryption, you can use a commercial or freeware utility that performs 7Z encryption with AES 256. For Windows, WinZip is the most popular. For macOS, Keka does a great job.
Which is the best compromise? I think that is a bit like asking what is a good compromise between chocolate ice cream and vanilla cake. It all comes down to your pain thresholds for cost, ease of use, level of security, and need for the other party to have the same setup.

by Marc Mintz | Sep 24, 2018
A: Antivirus is only a very small piece of the security and privacy puzzle – it doesn’t specifically protect against hackers. It protects against malware. Some of that malware may be under the control of hackers, some not. With or without antivirus, you still have work to do to protect your data.
If you are going to run without antivirus, perhaps the most important step is to enable application whitelisting. With this, only approved applications can launch (malware would not be on the approved list). With macOS, this is enabled once a user account is changed to a Parental Control account. With Windows on a domain, you can use the Group Policy Editor. Windows systems not on a domain can use the Security Policy Editor. To make life a bit easier, you may want to try VoodooShield.
Next, you must enable full disk encryption to help prevent brute force attacks from accessing your storage device when you aren’t logged in. In macOS, this means enabling FileVault 2. In Windows, this would be BitLocker.
Now that your drive is encrypted, make it even more difficult to crack your login password by using a strong password. Bare minimum of 15 characters.
And of course, NOBODY else will ever know your login password.
To ensure your email isn’t intercepted and read, you will need to have end-to-end encrypted email. The easiest way to do this is by getting a ProtonMail account.
As most of us communicate primarily by instant messaging and voice nowadays, it’s important to ensure these are also end-to-end encrypted. My favorite for this is Wire.
One area few give thought to is their social media presence. Far too much personal and sensitive information can be harvested from a social media account. Facebook, Google, LinkedIn, Apple, and most others now give subscribers good control over who can see what. But it’s even more important not to put the data there in the first place. And if it is there, remove it. Schools, employers, governments, and criminals all are interested in what you have in place.
The last step for the DIY user is to get a VPN account and use it 100% of the time that you are online. This will prevent your data from being harvested off of your local network, as well as off the internet.
Following the above gives you a good handle on your security and privacy.
Next… secure your mobile devices. But that is for another blog.

by Marc Mintz | Sep 24, 2018
A: Yes, otherwise they would not be able to authenticate your password on the next visit.
A quality site will store your password in an encrypted format, so if the site is compromised and the password database accessed, it is if no use. Unfortunately, this is by no means universal.
As a side note… Over 500,000 internet accounts are hacked every day! Because of this, it is vital to protect your data that is stored with online and brick-and-mortar businesses. Not a bad idea to mark your calendar to check every month if any of your accounts have been hacked. This is done by visiting:
- https://haveibeenpwned.com
- https://hacked-emails.com
These sites monitor such breaches. Their databases overlap, so best to check both.






















