
by Marc Mintz | Sep 19, 2022
Just when you thought it was safe to go back into the water.
Oh, wait. Wrong movie!
Do you have a credit card? Do you have a cell phone? Of course you do! And if a bad actor gains access to both of these, they have found an effortless way to gain full control over your credit card account.
The Hack
This hack was discovered when the bad actor was caught in the act at in the locker room of a gym. The process works like this:
- The bad actor (BA) opens lockers (at least at the gym) to gain physical access to then victims phone a credit card.
- BA uses their phone to attempt log in to your credit card account, tapping the “Forgot my password” or “Reset my password” button.
- An authorization code is sent to the victims cell phone.
- IF (big if) the victim has configured their phone to display messages while in Lock Screen mode, the authorization code is clearly visible to BA.
- BA enters the authorization code on their phone. This gives BA the opportunity to change your password, phone number, email address, and all other vital information.
- At this point, BA has full control over victims credit card account.
The Fix
Fortunately, the fix is straightforward and simple. All that need be done is to prevent messages from displaying on your Lock Screen. If you have followed me for any time, you know I’m a fan of not allowing ANYTHING to display on the Lock Screen.
For those of you who have just upgraded to iOS 16, this can be done from Settings > Notifications > Messages > disable the Lock Screen option. It is OK to leave Notification Center and Banner notification enabled.
For Android users, open Settings > Privacy > Notifications on Lock Screen > enable Don’t show notifications at all.
50% DISCOUNT ON ALL PRACTICAL PARANOIA BOOKS
IOS 16 AND IPAD 16 ARE NOW AVAILABLE
And so are the vulnerabilities to your device, data, and communications!
iOS 16 is the MUST HAVE upgrade for your iPhone and iPad. In addition to dozens of new features, iOS 16 has dramatically improved the options for your cybersecurity and internet privacy.
But you need to know HOW to properly configure your device to ensure your security.
Practical Paranoia Security Essentials has been doing just that for over 8 years at the best-selling, easiest, most comprehensive guid to securing data and communications on your home and office devices.
And from now until September 30, 2022, ALL Practical Paranoia Live! Edition books are 50% off!
Visit https://thepracticalparanoid.com to order at half price today. Just enter discount code “50” at check-out.
All Practical Paranoia Security Essentials books are available in paperback, kindle, and Live! editions.
Live! editions are exact replicas of the paperback and kindle editions, made available through Google Drive. This is the version used by Universities, trade schools, and high schools, and is now available to everyone. Its advantages include: Always available on any device with a browser and internet connection, and automatically and constantly updated as the OS, applications, and best practices evolve.
Questions, call +1.505.453.0479
![]()

by Marc Mintz | Aug 26, 2022
As reported in the August 25, 2022 edition of AppleInsider (https://appleinsider.com/articles/22/08/25/google-tracks-39-types-of-personal-data-apple-tracks-12), of the five major Big Tech firms, Google tracks more personal data than any other, and Apple tracks the least.
Google was found to track 39 data points per user, Twitter tracks 24, Amazon 23, Facebook 14, and Apple 12. According to the report, Apple tracks only data that is required to maintain the user account.
Unfortunately, there is no documentation on what data points are tracked.
WHY DO YOU CARE?
Perhaps you don’t care. But if you do, this information is important so that you can make fit decisions and choices for how you use your computer, software, and internet.
WHAT CAN YOU DO?
Although I’ve written 18 books on what you can do about personal data tracking, I’m also not foolish enough to think everyone will rush out and buy an armful of them (but please do). There are some simple steps anyone can take to stem the hemorrhaging of your data into government and advertiser servers:
- Use a privacy-centered browser. These include: Safari, Brave, and Firefox. All free.
- Use a quality VPN (Virtual Private Network) anytime you are online. My personal choice is NordVPN.
- Use a unique and strong password (15 or more characters) for every website and service.
- Use a quality Password Manager to store your overflowing list of unique and strong passwords. My personal favorite is Bitwarden. $10/year.
- Enable 2-Factor Authentication (also called Multi-Factor Authentication or One Time Use Password) for every site and service that provides for it. Then use Bitwarden to generate your 2-Factor Authentication codes.
- Use end-to-end encrypted text, phone, and video conference. My personal choice is Signal. Free.
- Use a quality anti-malware utility. My personal choice is Bitdefender.
- Only download software from legitimate sources. This is usually restricted to either the developer or the Apple Store, Google Play Store, or Microsoft Store.
- Verify at least weekly that your operating system and applications are current.
- Review your security and privacy settings for each of your social media platforms.
WANT TO BE PROTECTED LIKE THE PROFESSIONALS?
Practical Paranoia Security Essentials books have been the best-selling, easiest, and most comprehensive DIY guides for Android, ChromeOS, iOS, macOS, and Windows for nine years. Written by cybersecurity and internet privacy professionals for new and non-technical users, the reader is taken through an illustrated step by step process to secure their data in the same way the government secures their systems. We’ve made it so easy that anyone can confidently do it!


by Marc Mintz | Aug 24, 2022
I normally don’t post any of the daily cybersecurity alerts that post my desk. If I did, I would quickly fill up my 4TB local storage! But this is significant enough to warrant attention.
Hikvision is a highly popular camera manufacturer that is found around the world, with the USA having the second largest implementation–often as security video cameras. A severe security vulnerability was found last year, but it was reported 20220823 that over 80,000 of these units have not yet had their software updated.
Without the software security patch, these cameras are easily accessible by governments, criminals, and your everyday troublemaker.
To quote from the original source material:
Last year, Hikvision resigned from the Security Industry Association (SIA), the largest trade organization for surveillance vendors, after being accused of working with the Chinese Army on research to improve the ‘lethality’ of missiles.
Due to the one-two punch of the gaping and continuing vulnerability, and that Hikvision has resigned from the SIA, we can not recommend their use. We do recommend that should you have a Hikvision video camera in use, replace it ASAP.
Original source material: https://therecord.media/experts-warn-of-widespread-exploitation-involving-hikvision-cameras/

by Marc Mintz | Dec 4, 2021
A: VPN was initially designed to be used by computers. As such, there are software and network drivers to install and configure. The problem with IoT devices (Internet of Things, such as wireless thermostats, webcams, remote doorbells, wireless garage door openers, etc.) is that with almost no exceptions, developers have not included an option to add 3rd-party software and drivers. So by themselves, IoT devices cannot be secured.
BUT…
What if we were to do the following:
- Create an encrypted wi-fi for the IoT device to communicate on between your router and the IoT device.
- Enable VPN on the router, so that IoT data is encrypted between your router and your VPN provider.
Doing so makes it exceptionally difficult for your IoT data stream to be intercepted and harvested. No more threat of bad actors snooping on your home or business webcam, or remotely unlocking your digital door locks.
What Can We Do?
Encrypted Wi-Fi
The first step is to ensure your Wi-Fi router is configured properly for secure, encrypted networking.
The current encryption protocol of choice is called WPA3. Unfortunately, it has only been a standard for a year. There are few routers available to support it, and fewer IoT devices supporting it. However, I strongly recommend upgrading to a modem capable of WPA3 so that it is available as you upgrade your networkable devices.
My preference is for the ASUS brand of what are called Wi-Fi 6 or 6e routers. These are much faster than the previous generation, and support WPA3 and WPA2. I will use screenshots from the ASUS GT-AXE11000.
- Open the router control panel.
- From the sidebar select Wireless.
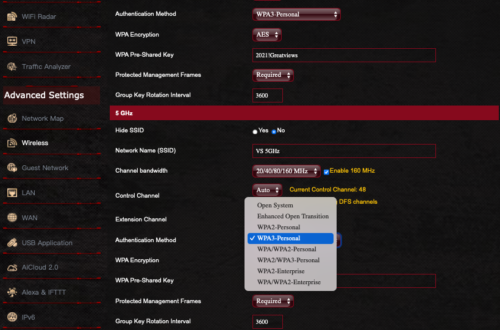
- Scroll down to the Wi-Fi channel you want to use for your IoT devices.
- Tap the Authentication Method. You will see a pop-up menu of all the available encryption options.
- Select WPA3-Personal, then configure the password.
- Save your changes.
- Test your IoT devices, computers, tablets, and mobile phones to determine if they can connect to WPA3.
- If all connect, we have rainbows and unicorns. If some devices cannot connect, you may need to change your Authentication Method to WPA2/WPA3.
- NOTE: Under no circumstances should you need to use WPA. This is a recipe for disaster. WPA has been broken, and any kid with 10 minutes of internet search will find the way to do it. Although WPA2 has also been broken, it is a more complex process.
Configure Your Router for VPN
The next step is to configure your router to connect to the internet via VPN. In this strategy, all traffic leaving the router is encrypted.
NOTE: Many mid-grade routers lack the ability to add VPN. This is a great time to invest in a modern, high-quality router that can add VPN, uses WPA3, and supports Wi-Fi 6.
- Subscribe to a quality VPN provider. I personally use NordVPN.
- From your VPN provider website, download their opvn file. This is the driver to be added to your router.
- Open your routers control panel page.
- From the sidebar, select VPN.
- From the tabs, select Fusion VPN.
- Under the Server List section, tap Add Server.
- In the Add Server window, select OpenVPN tab.
- Enter your VPN subscription username and password.
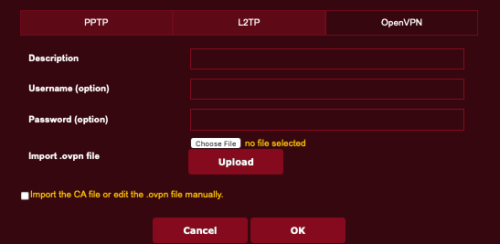
- Tap the Choose File button, then locate and select the opvn file downloaded in step 2.
- Tap the Upload button to upload the opvn file to your router.
- Tap the OK button.
- Returning to the main VPN page, in the Exceptions List area, tap the Add Exceptions.
- In the Create New Policy page, from the Client Name field, tap the drop down arrow to see all devices connected to your router.
- Select one that you wish to be protected by VPN.
- In the Connection Name field, select the name of the VPN policy you created in step 8.
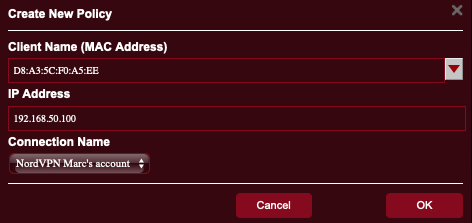
- Tap the OK button.
- Repeat steps 12-16 for every other device to be protected by VPN.
Yes, there are a lot of steps, but they are all easy, and the entire process may take under 10 minutes – AND you get to secure all your devices with VPN.
![]()

by Marc Mintz | Dec 4, 2021
A: Get 100 consultants in a room, end up with 100 opinions.
A bit of background information for those not familiar with Tor. Tor was created by the US Navy as a method to create secure, anonymous internet communications. It was soon after released from restricted government use for use by anyone.
The way Tor works is it is a network – called the “Onion Network” – that consists of three gateways that anyone using Tor must pass through. This includes an entry node, middle node, and exit node. All traffic over Tor is encrypted, and because the exit node knows nothing about user data from the entry node, the data is well anonymized. The user needs to use a browser that understands how to use the Onion Network. The officially recognized browser for use is called the Tor Browser.
From my perspective, I can’t recommend the use of Tor at this point. My reasons are:
- Due to the need to pass through 3 separate nodes, with encryption/decryption occurring at each, there is a huge latency (delay) introduced. This may slow down your internet work by as much as 4-10x.
- The US government (and probably many other governments) have their own nodes in play. If you control a node, you have access to the decrypted data.
- For the past few years a rogue player has installed around 900 nodes – out of a total of 9,000-10,000 total nodes. This one bad actor controls up to 10% of all nodes. Given that when using Tor you have to pass through 3 nodes, chances are around 30-35% your data will pass through one of theirs.
- The entire Tor node system is volunteer, and from all reports, poorly managed and supervised. I can very well see that at least 50% of all nodes are controlled by bad actors.
What to Do
Instead of relying on Tor, I very strongly recommend the 24/7 use of a quality Virtual Private Network service (VPN). With VPN, all of your internet traffic is encrypted as it exits your device, where it travels to the VPN provider, is decrypted, and sent on its way. This prevents harvesting of your data by someone snooping on your Ethernet, Wi-Fi, or cellular connection, your Internet Service Provider (ISP), and anyone else up to the VPN provider. And since your data stream is intermingled with potentially thousands of other users as it leaves the VPN provider, it is impossible to isolate your data.
In addition, when using a quality VPN, your internet traffic is only slightly impacted by the encryption/decryption process – in fact, many users report their internet speed increases when using VPN, as a quality VPN can block some unwanted traffic from hitting you.
There are thousands of VPN providers available. Perhaps the majority are not quality providers and should not be trusted. My go-to vendor of choice is NordVPN at https://nordvpn.com.














